To really lock down your Wi-Fi network, you need to tackle two things right away: change your router's default admin password and switch on the strongest encryption you can, which is WPA3. Getting these done first closes the most common backdoors attackers use and builds a solid foundation for your network's security.
Building Your First Line of Digital Defense
Leaving your Wi-Fi unsecured is like leaving your front door wide open. It’s an open invitation for anyone to walk in, snoop on your data, hog your internet, or even use your connection for malicious activity. The good news is that securing it doesn't require a master's degree in IT—just a few intentional steps.
It all starts with strengthening your router's login and encrypting the data flying through the air.
So many people forget the most basic step: changing the router's default login. Routers come from the factory with generic credentials like "admin" and "password" that are well-known and incredibly easy for anyone to guess. Leaving them as-is is a huge security hole, basically handing over the keys to your entire network. Make this the very first thing you change.
The infographic below really drives home these foundational security steps, from ditching default logins to embracing modern encryption.
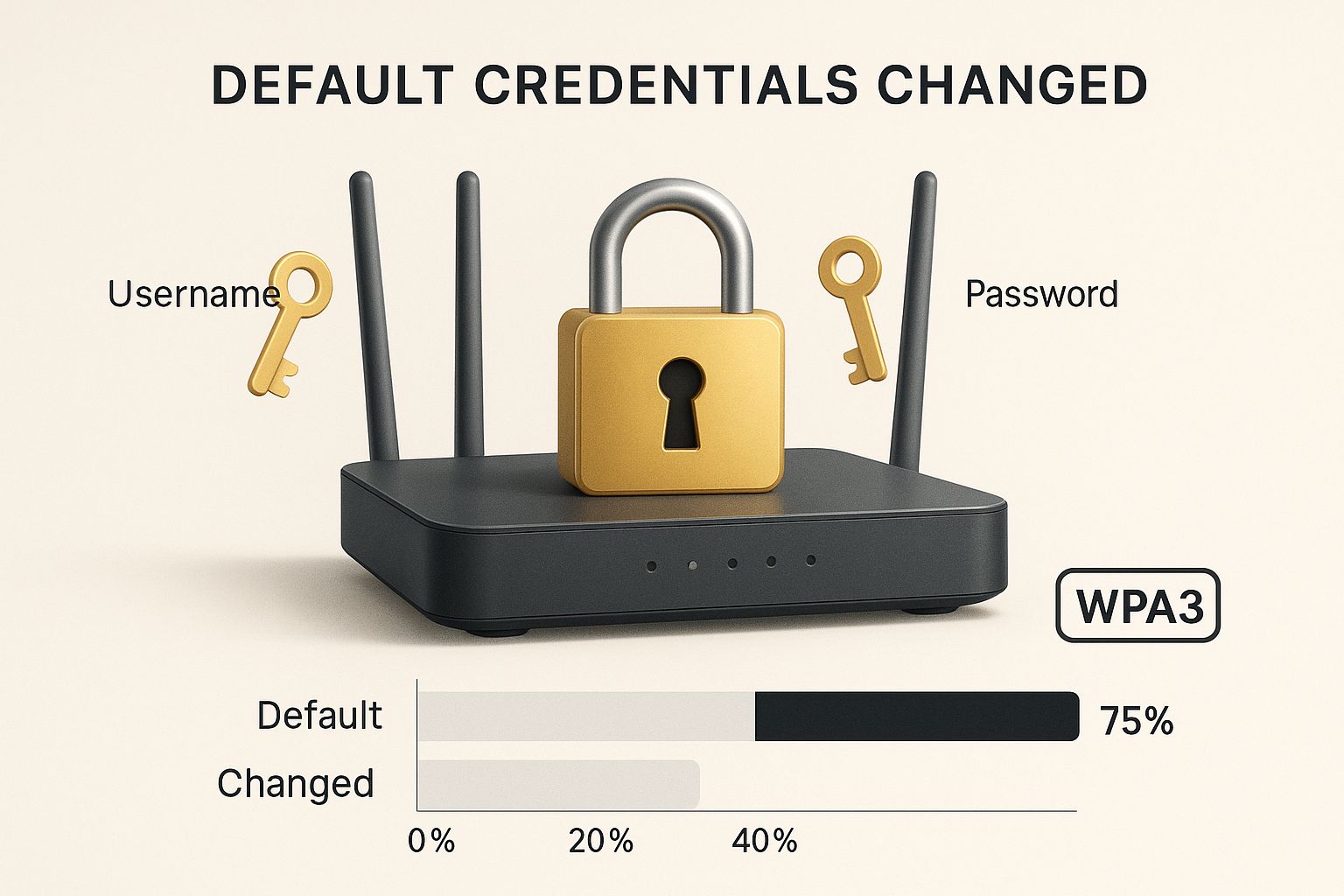
Think of it this way: a strong password and up-to-date encryption are the deadbolts on your digital door. They are what keep intruders out.
Choosing the Right Encryption Standard
Once you've secured the admin login, your next move is to encrypt your data. This process essentially scrambles all the information sent over your Wi-Fi, turning it into unreadable gibberish for anyone trying to eavesdrop. You'll find this option buried in your router’s wireless security settings.
When you get there, you'll likely see a few different encryption options. They are definitely not all created equal.
- WEP (Wired Equivalent Privacy): This is ancient technology. It’s so weak it can be cracked in a matter of minutes. Never, ever use it.
- WPA (Wi-Fi Protected Access): A step up from WEP, but it’s also outdated and has known weak points. It's best to avoid this one, too.
- WPA2 (Wi-Fi Protected Access II): This was the gold standard for years and is still very common. It's decent, but it has some vulnerabilities to more sophisticated attacks.
- WPA3 (Wi-Fi Protected Access III): This is the current champion. WPA3 offers much stronger protection against password-guessing attacks and provides robust, modern encryption across the board.
If you want a quick side-by-side look, this table breaks down the key differences between the two most relevant options, WPA2 and WPA3.
WiFi Encryption At a Glance: WPA2 vs. WPA3
| Feature | WPA2 (Still Common) | WPA3 (Recommended Standard) |
|---|---|---|
| Password Protection | Vulnerable to offline dictionary attacks. | Strong protection against brute-force attacks, even with weak passwords. |
| Forward Secrecy | Not required; past traffic can be decrypted if the key is compromised. | Mandatory; past traffic remains secure even if the password is stolen. |
| Public Network Security | Open networks are unencrypted and highly risky. | Individualized data encryption, making public Wi-Fi much safer. |
| Ease of Connection | Standard password entry. | Simplified connection process for devices without a display (IoT). |
Ultimately, choosing WPA3 is a no-brainer if your hardware supports it. It’s simply the most secure option available today for protecting your wireless traffic.
A 2025 industry analysis found something pretty startling: even with WPA3 available, over 75% of networks around the world are still running on the older WPA2 protocol. This exposes a massive number of people to well-known threats, showing a real disconnect between the security tools we have and what's actually being used.
Your goal should always be to use WPA3. If your router is older and doesn't support it, WPA2 with AES encryption is the bare minimum. Seriously consider upgrading your router, though—it’s a small investment for a massive security boost.
For a deeper dive into the "why" behind these security measures, our guide on https://www.gtcomputing.com/what-is-network-security/ is a great resource for understanding the core concepts.
Practical Steps to Enhance Your WiFi Security
So, how do you actually change these settings? It's pretty straightforward. You'll log into your router's admin page by typing its IP address into your web browser. From there, look for a "Wireless" or "Security" tab to update your encryption type and set a new, strong password.
For even more in-depth advice, check out these expert tips to protect your business Wi-Fi network.
By focusing on these two critical defenses—a unique admin password and WPA3 encryption—you’re building a formidable barrier against most common cyber threats. You'll turn your network from a potential weak spot into a secure and reliable asset.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
Advanced Router Settings That Harden Your Network
You've already built a solid defensive wall by locking down your router’s admin access and switching to strong WPA3 encryption. That’s a fantastic start. Now, let's go a level deeper and fine-tune some of the more advanced settings. Think of these adjustments as adding watchtowers and secret passages—they make your network not only tougher to breach but also much harder for outsiders to even find in the first place.
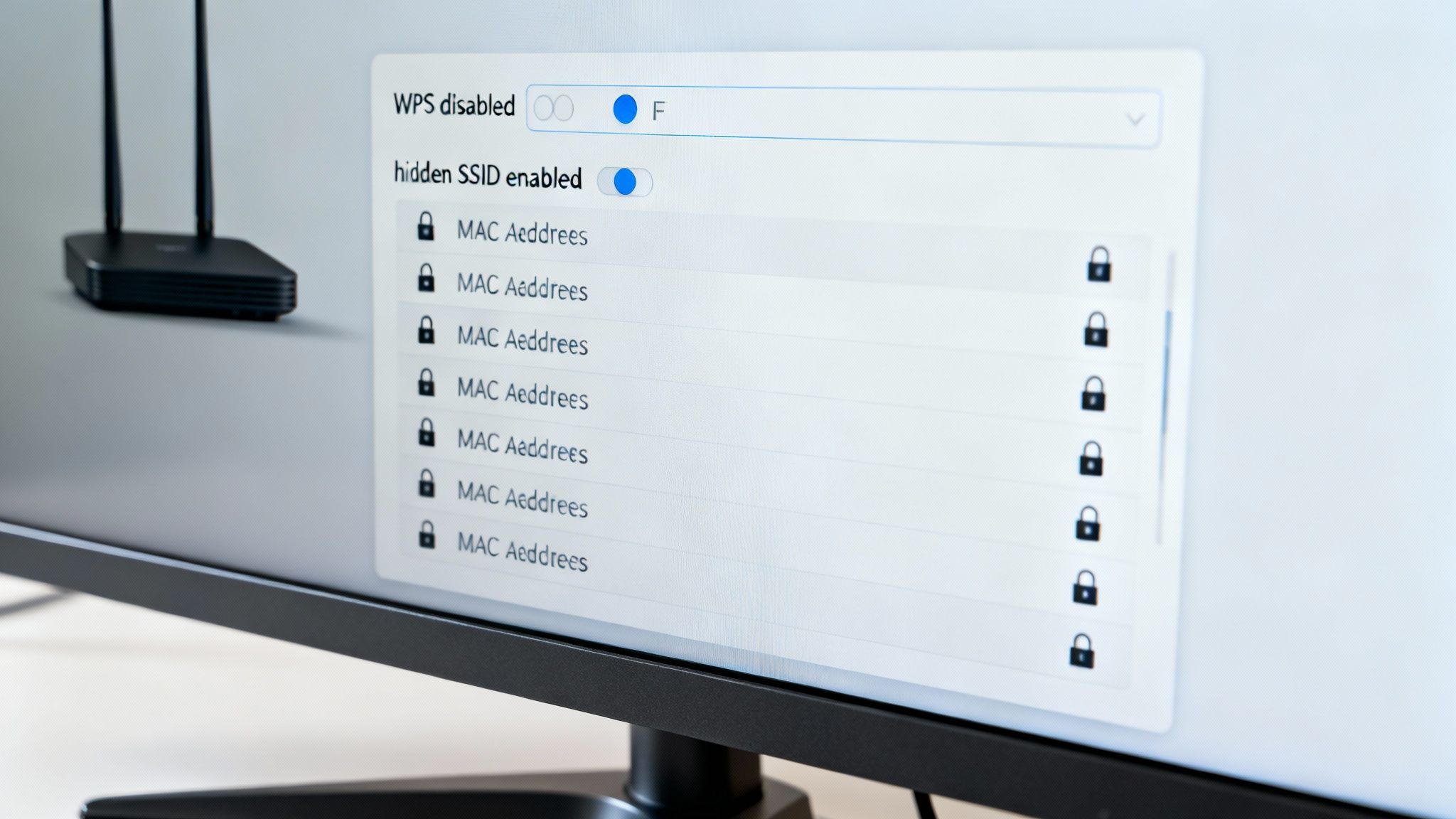
We're moving from basic security to proactive defense here. Each of these settings closes a potential loophole that attackers love to exploit, hardening your network against more determined threats.
Disable Wi-Fi Protected Setup (WPS)
First on the chopping block is Wi-Fi Protected Setup (WPS). It was designed for convenience, letting you connect a new device just by pushing a button on the router. It sounds great in theory, but in practice, WPS has a long history of security flaws. These vulnerabilities can be cracked with brute-force attacks, giving an intruder a direct line into your network.
Honestly, connecting a new device with a password is so simple these days that the minor convenience of WPS just isn't worth the risk. Disabling it is a quick and easy win. Dive into your router's wireless settings—you'll probably find it under a "WPS" or "Device Connection" tab—and just turn it off. You've instantly closed a well-known backdoor.
Hide Your Network From Plain Sight
By default, your router broadcasts your Wi-Fi network's name—its SSID (Service Set Identifier)—for all to see. This is what allows your phone or laptop to easily spot it in a list of available networks. The problem? It also advertises your network's existence to everyone else in range, including people looking for a target.
Why not make your network "invisible"? By disabling the SSID broadcast, your network's name will no longer pop up in those lists. Someone would have to know its exact name to even try to connect. This is a simple way to deter casual snoops and the automated hacking tools that are constantly scanning for easy targets.
To hide your SSID, here's the game plan:
- Log into your router's administration panel.
- Head over to the main wireless settings section.
- Find an option like "Enable SSID Broadcast," "Visibility Status," or something similar.
- Uncheck that box, save your changes, and you're done. Your existing devices will stay connected, but any new ones will need you to manually type in both the SSID and the password.
Hiding your SSID is a great layer of "security by obscurity." It won’t stop a dedicated hacker, but it effectively makes your network a much less obvious target, encouraging them to move on to easier prey.
This move is especially smart for a small business or home office where you have a set number of devices. It puts up a simple but surprisingly effective hurdle for anyone trying to get onto your connection without permission.
Use MAC Address Filtering for an Exclusive Guest List
If you want an even more granular level of control, it's time to look at MAC address filtering. Every single device that can connect to a network—your laptop, your phone, that smart TV—has a unique Media Access Control (MAC) address. You can think of it as a permanent serial number for its network hardware.
With MAC address filtering, you can create an exclusive "allow list" of devices that are permitted to join your network. It's like having a bouncer at the door. Even if someone steals your Wi-Fi password, their device won't be able to connect unless its MAC address is on your approved list.
Getting this set up involves a couple of steps:
- Find the MAC addresses: Dig into the "About" or "Network Settings" section of each of your devices to find its MAC address. Jot them down.
- Add them to your router's list: In your router's security settings, find the MAC filtering section and manually enter the addresses for every trusted device.
This method adds a really strong barrier. Now, a truly determined attacker with advanced tools could potentially "spoof" a MAC address, but that's a lot of work. That’s why MAC filtering is best used as part of a layered security approach, not as your only defense. While managing individual MAC addresses can get complicated in a large office, it’s a highly effective tactic for homes and small businesses.
For larger spaces that need consistent coverage and security, you might be interested in a solution for distributed Wi-Fi that simplifies management while maintaining robust protection.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
Keeping Your Wi-Fi Secure for the Long Haul
Let’s be honest, setting up a secure Wi-Fi network isn't a "set it and forget it" kind of deal. It’s more like tending to a garden; it needs regular attention to stay healthy. Once you've got the basics down, the real work begins with consistent maintenance and a little bit of vigilance.
Think of it this way: you wouldn't leave your front door unlocked for months on end, right? The same logic applies to your digital front door. This ongoing care really boils down to two simple but powerful habits: keeping your router's firmware fresh and keeping a close eye on who’s connected to your network. These routines are what keep your network safe day in and day out.
Your Router Needs Updates, Too
Every router runs on its own internal software, called firmware. It’s the brains of the operation, telling the hardware what to do. And just like your phone or computer, that software needs to be updated. Why? Because these updates almost always include patches for security holes that have been discovered since the router was made.
Cybercriminals absolutely love finding routers with outdated firmware. It’s one of the easiest ways for them to sneak into a network. When a manufacturer like Netgear or Linksys releases an update, they’re essentially fixing a known vulnerability. If you ignore it, you’re leaving a welcome mat out for attackers.
Fortunately, checking for an update is usually pretty straightforward.
- First, log into your router's administration page. This is the same place you went to change the network name and password.
- Next, look for a section called something like "Firmware Update," "Router Update," or maybe it’s tucked away under "Administration" or "System Tools."
- Most modern routers have a simple "Check for Updates" button that will find and install the latest version for you. If yours is a bit older, you might need to pop over to the manufacturer's support website, find your model, and download the update file to install it manually.
I tell all my clients to set a calendar reminder to check for new firmware once a month. It’s a five-minute task that pays huge dividends for your security.
Think of firmware updates as changing the locks on your digital doors whenever a new master key is discovered by criminals. It’s a non-negotiable part of knowing how to secure your Wi-Fi network properly.
This small bit of upkeep ensures your router has the latest defenses against whatever new threats are out there.
Keep an Eye on Who's on Your Network
The second piece of the puzzle is simply knowing who’s connected to your Wi-Fi at all times. An unfamiliar device on your network could just be a neighbor borrowing your internet, but it could also be an attacker trying to listen in on your activity. You can't be too careful.
Most routers have a page in their admin settings that shows you a list of every device currently online. It's usually called "Attached Devices," "Device List," or "Clients." You'll see device names like "Jane's MacBook Pro" or "Living Room Roku" along with a unique identifier called a MAC address.
Make a habit of pulling this list up once a week.
- Do a quick audit. Can you account for every single device on that list? It helps to name your own devices clearly in their settings so you can recognize them instantly.
- Look for red flags. Is there an "unknown device" or a Samsung phone model when everyone in your house uses an iPhone? That’s something to investigate immediately.
- Act fast if you see an intruder. The moment you spot a device that shouldn’t be there, your first move is to change your Wi-Fi password. This will boot everyone off the network. You'll have to reconnect your own devices with the new password, but so will the intruder—and they won't have it.
This routine check is your network’s own little security camera. By seeing who's coming and going, you can spot trouble and kick it out before any real damage is done.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
Why You Need a Guest Network for IoT Devices
Dumping every single smart device onto your main Wi-Fi network might feel simple, but from a security standpoint, it’s like leaving your front door wide open. Think about it—you've got smart thermostats, cameras, speakers, and maybe even a connected coffee maker. Every one of those gadgets is a potential back door for an attacker.
This is where a simple yet powerful strategy comes into play: network segmentation.
The idea is to create a separate guest network just for your Internet of Things (IoT) devices. Doing this isolates them from your primary network, which is where your sensitive stuff—like your work laptop and personal phone—lives. If a hacker manages to break into your smart TV, they'll be stuck on the guest network, unable to hop over and sniff around your financial records or client files.

It’s a digital firewall. Any potential breach gets contained to the less critical network. This isn't just a neat trick; it's a fundamental step in securing a modern Wi-Fi network that's cluttered with all sorts of connected devices.
The Growing Threat from Your Smart Gadgets
You might be wondering if your smart toaster is really that big of a deal. The honest answer is yes. Many IoT devices are designed for convenience and a low price point, not for rock-solid security. They often come with ridiculously simple default passwords, rarely get security updates, and can sit for years with known, unpatched flaws.
The scale of this problem is genuinely massive. Forecasts show that by 2025, one in three data breaches will be traced back to a compromised IoT device. We also know that over half of all these gadgets have critical vulnerabilities just waiting for a hacker to find them.
Even worse, unpatched firmware is behind a staggering 60% of IoT security breaches. The trouble is, keeping them all updated is a nightmare because of the sheer variety of devices and spotty support from manufacturers. You can dig into more IoT security stats to really grasp the scope of the threat.
Setting up a guest network is your single best defense against this growing threat. It acknowledges the inherent weakness of many IoT products and intelligently quarantines them away from what truly matters.
This one proactive step dramatically shrinks your "attack surface," making it much, much harder for one vulnerable gadget to cause a complete disaster.
How to Set Up and Organize Your Guest Network
The good news is that most modern routers make this incredibly easy. You can usually get a guest network up and running in just a few clicks inside your router's admin panel.
Here's the typical process:
- Log into your router's settings. You’ll do this by typing its IP address into your web browser.
- Find the "Guest Network" section. This is often located under the main "Wireless" or "Wi-Fi" settings tab.
- Enable the guest network. Make sure to give it a distinct name (SSID) so you can tell it apart from your main network. Something like "Smith_Guest" or "SmartHome-IoT" works well.
- Set a strong, unique password. Don't get lazy and reuse your main Wi-Fi password!
- Save your changes. Your router will likely restart, and you'll have a second, isolated network ready to go.
With the guest network active, the last piece of the puzzle is to move your devices over. Disconnect all your IoT gadgets—the smart speakers, TVs, security cameras, and thermostats—from your main Wi-Fi and reconnect them to the new guest network. Your trusted devices, like your work computer, personal laptop, and smartphone, should be the only things left on your primary network.
Network Segmentation Strategy
This table offers a straightforward way to think about which devices go where to keep your network as secure as possible.
| Device Type | Recommended Network | Security Rationale |
|---|---|---|
| Computers & Smartphones | Main Network | These devices hold your most sensitive data and need the highest level of trust and protection. |
| Smart TVs & Streaming Sticks | Guest Network | Prone to vulnerabilities and rarely updated, making them a prime target for attackers. |
| Security Cameras & Doorbells | Guest Network | A compromised camera could give an intruder eyes and ears inside your property; isolation is key. |
| Smart Thermostats & Speakers | Guest Network | Often have minimal security features and can serve as an easy entry point to your network. |
By dedicating just a few minutes to creating and organizing a guest network, you're putting a professional-grade security tactic to work, protecting your most valuable digital assets from the weakest links in your smart home.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
What About When You're On the Go? Staying Secure on Public Wi-Fi
It’s great to have your home or office network locked down, but what happens when you step out the door? Public Wi-Fi at coffee shops, airports, and hotels is a modern convenience we all rely on. The problem is, these networks are a Wild West of security threats. When you hop onto that free connection, you're sharing digital space with strangers, and not all of them have good intentions.
The sheer number of public hotspots is staggering—it's expected to hit over 643 million worldwide by 2025. But convenience has a cost. Nearly 40% of Americans have run into a security problem after using public Wi-Fi. What’s really telling is the confidence gap: over 65% of us worry about the safety of these networks, but only one in five feel they could actually spot a malicious hotspot. You can dive deeper into these numbers with Panda Security's public Wi-Fi safety survey.
This all points to one thing: you need a solid game plan for when you're away from your own trusted network.
The Common Dangers Lurking on Public Networks
When you connect to public Wi-Fi, you're walking into a few common cyber traps. The most classic is the "man-in-the-middle" (MitM) attack. Imagine a hacker sitting between your laptop and the coffee shop's router. They can silently intercept, read, and even change the data flying back and forth. This means your passwords, credit card details, and private messages are all up for grabs.
Then there's the equally sneaky "evil twin" attack. In this scenario, a hacker sets up their own hotspot with a name that looks totally legit, like "Airport_Free_WiFi" or "Hotel Guest." You connect, thinking you're safe, but you've just handed the attacker complete control over your internet traffic. It's a simple, low-tech trick that works far too often.
Your Best Defense: The Virtual Private Network
The single most powerful tool you can have in your public Wi-Fi toolkit is a Virtual Private Network (VPN). A VPN is simply an app that wraps all your internet traffic in a secure, encrypted tunnel.
Think of it like this: your data is traveling on a public highway. Without a VPN, it's out in the open. With a VPN, it's inside an armored car. Even if a hacker is watching the road, all they see is the armored vehicle—the contents are completely hidden.
When you flip on your VPN, it scrambles your data so it's unreadable to anyone else on the network. This encryption is your shield against both man-in-the-middle and evil twin attacks. Even if you accidentally connect to a hacker's hotspot, they won't be able to make any sense of your information. It's an absolute must-have for anyone who ever connects to Wi-Fi outside their home.
If you take away one thing, let it be this: Always turn on your VPN before you connect to public Wi-Fi. Don't check your email, don't scroll through social media, don't do anything until that secure tunnel is active. Making this a habit can save you from a world of trouble.
How to Pick a VPN You Can Actually Trust
Not all VPNs are created equal. You’re essentially routing all of your internet activity through their servers, so choosing a reputable provider is critical.
Here’s what you should look for:
- A Rock-Solid "No-Logs" Policy: This is non-negotiable. A trustworthy VPN provider will have a strict, verified policy of not logging or tracking your online activity. This is the cornerstone of online privacy.
- Modern Encryption: Look for providers using strong encryption standards like AES-256. This is the same level of encryption used by banks and governments to secure their data.
- Good Performance: A VPN will always slow your connection down a bit—that’s just the nature of encryption. But a good one minimizes the impact. Check out recent reviews that specifically talk about speed and reliability.
- Plenty of Server Locations: Having servers in multiple countries is great for getting around region-locked content, but more practically, it means you can always find a fast, stable connection no matter where you are.
A quality VPN service is a small price to pay for genuine peace of mind. It’s the one tool that can turn almost any public hotspot into a safe place to work and browse.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
Common WiFi Security Questions Answered
When it comes to Wi-Fi security, a lot of the same questions pop up again and again. We've covered the big strategies for locking down your network, but let's dive into some of those specific "what if" scenarios that people often ask about.
Think of this as your go-to FAQ. We’ll skip the jargon and give you direct answers to help you make smarter decisions for your home or small business network.
Is Hiding My Network Name (SSID) Really Enough Security?
Hiding your SSID is a good first step, but you have to understand what it actually does—and what it doesn't. It's a layer of obscurity, not a true security barrier.
When you stop broadcasting your SSID, your network name vanishes from the list of available Wi-Fi connections on your neighbors' devices. This is great for discouraging casual snoops or so-called "wardrivers" who are just cruising for an easy, open network to hop onto.
But here's the catch: a determined attacker isn't going to be fooled. With the right software, they can easily scan for wireless traffic and uncover your "hidden" network's name.
Hiding your SSID is like taking the house number off your front door. It’ll confuse a casual visitor, but anyone who really wants to find you will figure it out. It's a worthwhile step, but it's no substitute for strong WPA3 encryption and a complex password.
So, go ahead and hide your SSID. Just don't ever make the mistake of thinking it's your only line of defense.
Should I Turn Off My WiFi When I'm Not Home?
This is a great question because it gets right to the core of reducing your "attack surface." The short answer is yes—if it's practical. If you're going on vacation for a week, shutting down your Wi-Fi is a brilliant move. An offline network can't be attacked. Simple as that.
For your daily routine, like heading to work, the security payoff is pretty small and might not be worth the hassle. Many smart home devices—thermostats, cameras, smart speakers—depend on that constant connection to run their schedules and automations. Turning the router off every day could throw a wrench in the works.
A good middle ground? Use a basic outlet timer for your router. You can set it to automatically power down late at night when everyone's asleep and switch back on in the morning. This shrinks the window of opportunity for attackers without you having to think about it every day.
Does My Internet Provider Help Secure My WiFi?
Your Internet Service Provider (ISP) is responsible for securing the connection to your house, but once that signal is inside, the security of your Wi-Fi network is almost entirely on you. The router they give you is just the gateway.
ISPs are getting better, and some now ship their routers with more secure defaults, like a unique, randomized password on the sticker instead of just "admin" or "password." Even so, you are the system administrator for that device. That means you're in charge of:
- Changing the default admin password needed to access the router's settings.
- Making sure the strongest encryption (WPA3) is turned on.
- Keeping the router's firmware updated to patch security flaws.
- Setting up a secure guest network for visitors and less-secure IoT gadgets.
Never assume your ISP configured your router for maximum security. You have to log in and check these settings yourself. Think of the ISP as the utility company that runs the power lines to your house; you're still the one who has to lock the doors and windows.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
Ready to Bring in an Expert?
We've walked through the key steps for locking down your Wi-Fi, from basic settings to more advanced strategies. Honestly, putting these measures in place will make you a much harder target for the average cybercriminal.
But let's be realistic. For a complex home office or any kind of business, a DIY approach can sometimes leave you with a false sense of security. How can you be sure you've covered all your bases? This is where professionals come in. They often start by understanding WiFi penetration testing to actively hunt for weak spots in your setup—the same ones an attacker would try to exploit—and fix them first.
Instead of losing hours to network configurations and troubleshooting, an expert can dial in your security and performance settings correctly right from the get-go.
For any business, handing this responsibility over to a team that provides managed IT services for businesses is often the smartest move. It means certified professionals are in your corner, handling the constant monitoring, patching, and threat management. It frees you up to focus on running your business.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com



