In today's interconnected business environment, a security breach is no longer a question of 'if' but 'when.' For small and mid-sized businesses, including professional practices like law firms and dental offices, the impact of an attack can be devastating. A single incident can lead to significant financial loss, crippling reputational damage, and prolonged operational chaos. However, building a formidable defense doesn't require a Fortune 500 budget. The key lies in a proactive and layered approach, implementing proven, strategic network security best practices that work in concert to protect your critical assets.
This guide moves beyond generic advice. We provide a detailed, actionable roundup of the 10 most critical security measures your organization must adopt right now. We will explore everything from foundational principles like robust access controls and employee training to advanced strategies like implementing a Zero Trust architecture. Each point is designed to equip you with the specific knowledge needed to transform your network from a potential liability into a secure fortress. By understanding and applying these concepts, you can significantly reduce your attack surface and enhance your overall resilience against cyber threats. To further explore actionable strategies for protecting your business, consider these additional insights on the 10 Essential Network Security Best Practices that complement the detailed items we will cover. Let’s dive into the essential practices that will secure your operations.
1. Zero Trust Architecture
The traditional "castle-and-moat" approach to network security, which trusts anyone inside the network perimeter, is dangerously outdated. Zero Trust Architecture (ZTA) completely upends this model with a simple but powerful principle: never trust, always verify. It assumes threats can originate from anywhere, both inside and outside the network, and therefore requires strict verification for every access request.
This framework is not about denying access but about ensuring every user and device is authenticated and authorized before gaining entry to applications and data. It operates on a need-to-know basis, granting only the minimum level of access required for a specific task. This approach significantly reduces the potential attack surface and limits an attacker's ability to move laterally within your network if a breach occurs.
The following concept map illustrates the three interconnected pillars that form the foundation of a successful Zero Trust strategy.
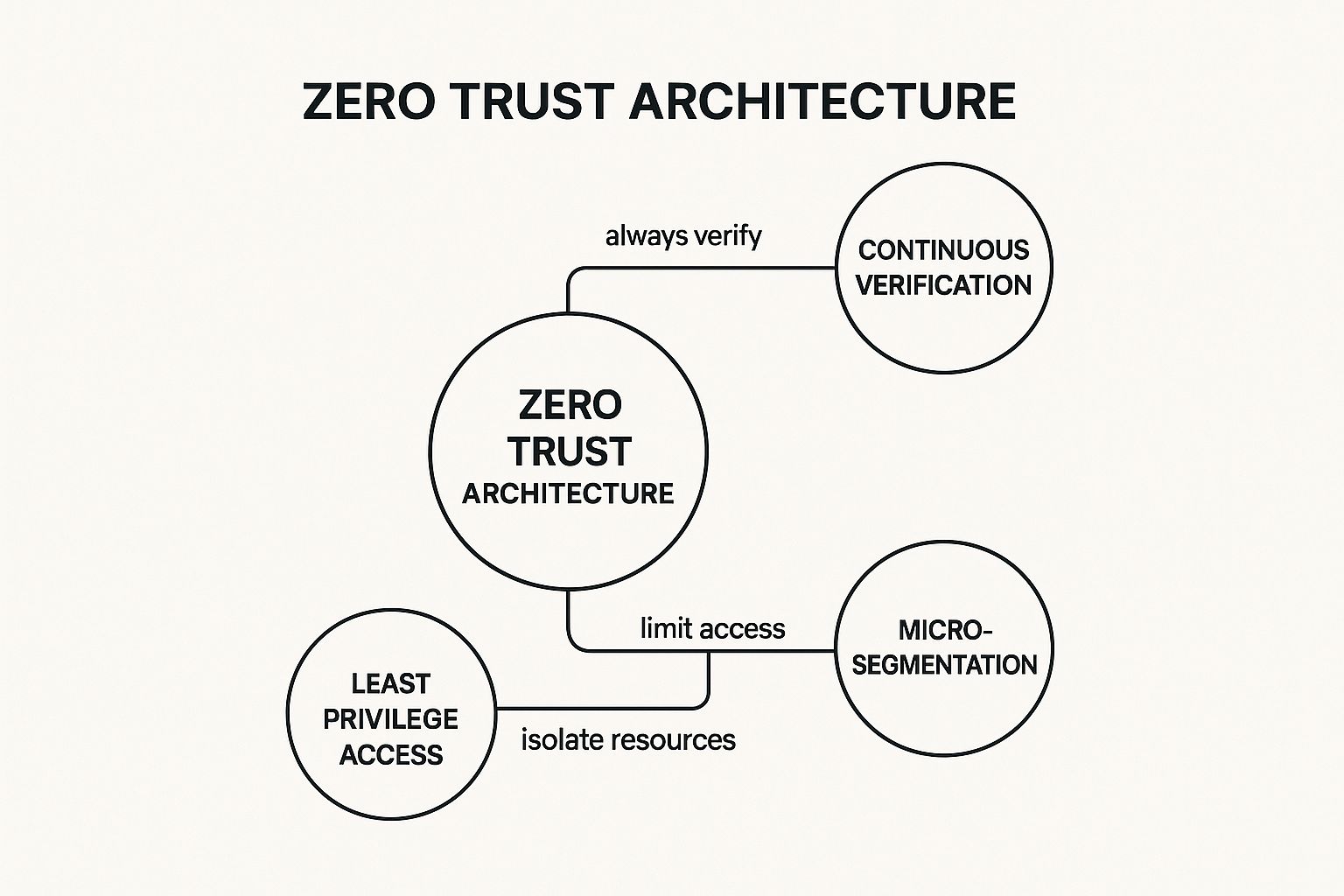
This visualization highlights how continuous verification, least privilege access, and micro-segmentation work together to enforce and maintain a secure environment.
How to Implement a Zero Trust Model
Shifting to ZTA is a strategic journey, not an overnight switch. For an in-depth understanding of this paradigm, delve into what Zero Trust Security entails. Start small by focusing on your most critical assets first.
- Map Your Assets: Begin by creating a comprehensive inventory of your data, applications, and infrastructure. Classify data based on sensitivity to understand what needs the most protection.
- Enforce Strict Access Controls: Implement multi-factor authentication (MFA) across all systems. Use identity and access management (IAM) tools to define granular, role-based access policies.
- Segment Your Network: Use micro-segmentation to create small, isolated zones within your network. This prevents unauthorized lateral movement, containing a potential breach to a single segment.
- Monitor and Adapt: Continuously monitor all network traffic and access patterns. Analyze logs to detect anomalies and refine security policies based on real-world activity.
By adopting a Zero Trust mindset, businesses can build a more resilient and adaptive defense, making it one of the most effective network security best practices for the modern threat landscape.
2. Regular Security Patches and Updates
Neglecting software updates is like leaving your front door wide open for cybercriminals. Regular security patches and updates are the systematic practice of keeping all systems, software, and applications current. This process remediates known vulnerabilities before attackers can exploit them, forming a critical layer of defense.
This proactive maintenance is one of the most fundamental network security best practices. Famous breaches, like the 2017 Equifax incident that affected 147 million people, often stem from a failure to apply a known patch. By establishing a routine for identifying, testing, and deploying updates, you effectively close security gaps identified by vendors and the global security community.

This image represents how consistent patch management acts as a robust shield, protecting your digital assets from emerging threats and vulnerabilities.
How to Implement a Patch Management Program
An effective patch management strategy requires consistency and structure, not just occasional updates. It's a continuous cycle of assessment and deployment that significantly strengthens your security posture.
- Automate Where Possible: Use automated patch management tools to ensure consistent and timely deployment across all devices. This reduces human error and ensures no system is overlooked.
- Prioritize and Schedule: Not all patches are equal. Prioritize updates based on Common Vulnerability Scoring System (CVSS) scores and the criticality of the system. Establish a regular schedule, like Microsoft's "Patch Tuesday," for routine updates.
- Test Before Deploying: Always test patches in a non-production or sandboxed environment first. This prevents compatibility issues or unintended downtime for your critical business operations.
- Maintain an Asset Inventory: You can't protect what you don't know you have. Keep an accurate, up-to-date inventory of all hardware and software assets to ensure everything is included in your patching cycle.
- Plan for Emergencies: Develop a rapid response procedure for critical zero-day vulnerabilities. This plan should allow you to bypass standard testing protocols to deploy an emergency patch immediately.
By integrating a disciplined patch management program, your business can dramatically reduce its attack surface and prevent catastrophic breaches caused by well-known, preventable exploits.
3. Multi-Factor Authentication (MFA)
A password alone is no longer a sufficient defense against sophisticated cyber threats. Multi-Factor Authentication (MFA) adds a critical layer of security by requiring users to provide two or more verification factors to gain access. This approach combines something you know (like a password), something you have (like a mobile phone or hardware key), and something you are (like a fingerprint or facial scan).
This layered defense means that even if a cybercriminal steals a password, they are still locked out without the additional verification factor. Microsoft’s own research confirms the power of this practice, reporting that enabling MFA blocks 99.9% of automated account compromise attacks. It is one of the single most effective network security best practices for protecting user accounts and sensitive data from unauthorized access.

The image above illustrates how combining independent credentials creates a more robust and resilient verification process, making it exponentially harder for attackers to succeed.
How to Implement Multi-Factor Authentication
Rolling out MFA effectively requires a thoughtful strategy that balances security with user convenience. For a detailed look at how to secure your accounts, consider the guidance offered by the Cybersecurity & Infrastructure Security Agency (CISA).
- Prioritize Critical Accounts: Begin your MFA rollout by securing your most sensitive accounts first. This includes administrative roles, executive accounts, and any user with access to financial or proprietary data.
- Choose Secure Factors: Whenever possible, use authenticator apps (like Google Authenticator or Microsoft Authenticator) or hardware security keys (like YubiKey) over SMS-based codes, which are vulnerable to SIM swapping attacks.
- Establish Clear Policies and Training: Develop a clear policy outlining when and where MFA is required. Provide employees with straightforward documentation and training to ensure a smooth adoption process and explain why this extra step is crucial.
- Monitor for Anomalies: Continuously monitor for suspicious MFA activity, such as repeated failed attempts or requests from unusual locations. These can be early indicators of a targeted attack against an account.
By making MFA a mandatory component of your security framework, you create a powerful barrier that significantly reduces the risk of account takeovers and data breaches.
4. Network Segmentation and Micro-segmentation
Treating your entire network as one large, open space is a significant security risk. Network segmentation is a fundamental practice that divides a computer network into smaller, isolated sub-networks or segments. This approach ensures that each segment functions as its own secure zone, drastically limiting an attacker's ability to move laterally across your infrastructure if one area is compromised.
Micro-segmentation takes this concept a step further, applying security policies to individual workloads and applications. This granular control creates an even more secure environment by isolating systems and services from one another, even if they reside on the same server. The infamous 2013 Target breach, where attackers pivoted from a compromised HVAC vendor network to the main payment systems, underscores the critical need for this security measure.

This visual shows how a once-flat network is divided into secure, logical zones, each with its own access controls, effectively building internal firewalls that contain threats.
How to Implement Network Segmentation
Implementing segmentation requires careful planning and a deep understanding of your network's data flows and assets. The goal is to enforce the principle of least privilege not just for users, but for network traffic itself.
- Identify and Classify Assets: Begin by mapping all your network assets, including data, devices, and applications. Classify them based on sensitivity and function to determine segmentation boundaries.
- Create Logical Segments: Group related assets into segments based on their purpose or risk profile. For instance, create separate segments for guest Wi-Fi, point-of-sale systems, and sensitive servers.
- Isolate High-Risk Devices: Place IoT devices and legacy systems that cannot be easily patched into their own heavily restricted segments to prevent them from being used as an entry point. More information on how to secure Wi-Fi networks can be found when you learn more about network security on gtcomputing.com.
- Control Inter-Segment Traffic: Use next-generation firewalls to inspect and control all traffic moving between segments. Enforce strict access rules, allowing only necessary communication.
By adopting segmentation, you create a more defensible and resilient network, making it one of the most powerful network security best practices for containing breaches.
5. Strong Password Policies and Password Management
Passwords remain the primary keys to your digital kingdom, and weak or compromised credentials are a leading cause of data breaches. A strong password policy moves beyond simply telling users to "make it complex." It establishes a comprehensive framework for creating, managing, and safeguarding credentials across the entire organization. This modern approach prioritizes real-world user behavior and known threats over outdated rules.
This strategy recognizes that the biggest vulnerability is often human error. Instead of enforcing frustrating rules like mandatory periodic changes, which often lead to predictable patterns, the focus shifts to creating long, memorable passphrases and using tools that automate security. By combining clear guidelines with technology like password managers, businesses can drastically reduce their risk of unauthorized access.
How to Implement Strong Password Policies
Adopting a modern password strategy is one of the most cost-effective yet high-impact network security best practices you can implement. The goal is to make security seamless for users while making it exponentially harder for attackers.
- Prioritize Length Over Complexity: Encourage users to create long passphrases (e.g., "Correct-Horse-Battery-Staple") rather than short, complex passwords. NIST guidelines now favor length, as it is a greater determinant of a password's resistance to brute-force attacks.
- Deploy an Enterprise Password Manager: Tools like Bitwarden or 1Password securely store credentials, generate strong, unique passwords for every service, and simplify secure password sharing among teams. This eliminates the dangerous habit of reusing passwords.
- Eliminate Mandatory Expiration: Following guidance from Microsoft and NIST, abandon forced periodic password changes unless a compromise is suspected. This prevents users from making small, predictable alterations to existing passwords.
- Check for Compromised Credentials: Integrate a service like Have I Been Pwned's API to proactively check if employee credentials have appeared in public data breaches and force a reset if a match is found.
- Move Toward Passwordless Authentication: Where possible, adopt more secure methods like biometrics (Windows Hello), security keys (FIDO2), or authenticator apps. This removes the password as a potential point of failure altogether.
By implementing a robust and user-friendly password management policy, you empower employees to become the first line of defense rather than a potential security liability.
6. Regular Security Awareness Training
While technology provides essential layers of defense, the human element remains a primary target for cybercriminals. Regular Security Awareness Training addresses this vulnerability by transforming your employees from potential security liabilities into a proactive line of defense. This practice involves ongoing education that equips your team to recognize, report, and resist cyber threats like phishing, social engineering, and malware.
The goal is to cultivate a security-first mindset across the entire organization. By teaching staff about the latest threats and safe computing habits, you build a "human firewall" that complements your technical security controls. This is one of the most cost-effective network security best practices, as a well-trained employee can thwart an attack that might otherwise bypass expensive software and hardware.
How to Implement Security Awareness Training
Effective training is a continuous program, not a one-time event. The key is consistent reinforcement and practical application. For a comprehensive approach, consider the programs offered by leading providers like KnowBe4, which specialize in building this human defense layer.
- Establish a Baseline: Start by running a simulated phishing test to gauge your team's initial susceptibility. This provides a clear benchmark to measure future progress.
- Conduct Regular, Bite-Sized Training: Schedule short, engaging training sessions (10-15 minutes) at onboarding and at least quarterly thereafter. Focus on relevant, real-world examples that resonate with your employees' daily tasks.
- Run Simulated Phishing Campaigns: Regularly send unannounced simulated phishing emails to test employee awareness. Provide immediate, educational feedback to those who click, explaining the red flags they missed.
- Track and Reinforce: Monitor key metrics like training completion rates, phishing simulation click rates, and the number of reported suspicious emails. Use this data to tailor future training and acknowledge positive security behaviors, not just punish mistakes.
By investing in your team's security knowledge, you create a resilient culture that significantly strengthens your overall network security posture against sophisticated and evolving threats.
7. Comprehensive Backup and Disaster Recovery Planning
A reactive approach to data loss can be catastrophic, leading to permanent data destruction, severe reputational damage, and even business failure. A comprehensive backup and disaster recovery (BDR) strategy ensures business continuity by systematically creating, testing, and maintaining secure copies of critical data and systems. This proactive practice is your ultimate safety net against ransomware, hardware failures, natural disasters, and simple human error.
Effective BDR is not just about making copies; it's about having a tested, reliable plan to restore operations quickly and efficiently. The infamous Colonial Pipeline incident in 2021 serves as a stark warning. While they had backups, their poor recovery procedures led to an extended outage and a multi-million dollar ransom payment. This highlights that a plan is only as good as your ability to execute it under pressure.
How to Implement a Resilient BDR Strategy
Building a robust BDR plan involves more than just software; it requires a disciplined, multi-layered approach. To explore tailored solutions, consider the benefits of a managed data backup service to handle the complexities for you. Start by defining your recovery objectives and then build your processes around them.
- Follow the 3-2-1-1 Rule: Maintain at least three copies of your data on two different media types, with one copy stored offsite and one copy that is immutable or air-gapped (offline and unreachable by attackers). This is a foundational principle of modern network security best practices.
- Test Restoration Regularly: Backups are useless if they can't be restored. Schedule and conduct quarterly restoration tests to verify data integrity and ensure your recovery procedures work as expected. Document the outcomes and refine your plan.
- Secure Your Backups: Implement immutable backups that cannot be altered or deleted by ransomware. Encrypt all backups both in transit and at rest, and use separate administrative credentials for your backup systems that are distinct from your primary domain admin accounts.
- Plan and Practice Recovery: Document your entire disaster recovery plan, including who is responsible for what. Conduct tabletop exercises with your team to walk through different disaster scenarios, identifying gaps and ensuring everyone understands their role.
8. Continuous Security Monitoring and Incident Response
Preventing every single security threat is impossible, but detecting and responding to them swiftly is not. Continuous security monitoring is the vigilant, real-time observation of all activity across your IT infrastructure. It involves collecting, analyzing, and correlating security event data to detect threats, anomalies, and policy violations as they happen.
This proactive detection is only half the battle. It must be paired with a formal incident response (IR) plan, which acts as a strategic playbook for when a security event occurs. A strong IR plan enables your organization to identify, contain, remediate, and learn from incidents, minimizing damage, downtime, and recovery costs. The 2017 Equifax breach, where data exfiltration went undetected for 76 days, is a stark reminder of why both detection and response are critical network security best practices.
How to Implement Continuous Monitoring and Response
Building this capability requires a combination of technology, processes, and people. A good starting point is the NIST Computer Security Incident Handling Guide, which provides a comprehensive framework for developing your plan.
- Deploy a SIEM Solution: Implement a Security Information and Event Management (SIEM) tool like Splunk, IBM QRadar, or an open-source option like the ELK Stack. This technology aggregates and analyzes log data from across your network, providing a single pane of glass for threat detection.
- Develop a Formal IR Plan: Create a documented plan that outlines roles, responsibilities, and communication channels. Define clear escalation procedures so everyone knows who to contact and what decisions they are authorized to make during a crisis.
- Create Incident Playbooks: For common threats like malware infections, phishing attacks, or unauthorized access, develop step-by-step playbooks. These guides ensure a consistent, efficient, and effective response, reducing human error under pressure.
- Practice and Refine: Don't let your plan sit on a shelf. Conduct quarterly tabletop exercises to simulate security incidents and test your team's response. Use these drills to identify gaps, refine procedures, and ensure everyone is prepared to act decisively.
9. Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR)
Traditional antivirus software, which relies on known virus signatures, is no longer sufficient to stop modern, sophisticated cyberattacks. Endpoint Detection and Response (EDR) provides a necessary evolution, offering integrated security that continuously monitors endpoints like computers, servers, and mobile devices for suspicious behavior. It moves beyond simple malware scanning to provide comprehensive threat detection, investigation, and automated response capabilities.
This advanced approach uses behavioral analysis and threat intelligence to identify complex attacks that might otherwise go unnoticed. Extended Detection and Response (XDR) expands this visibility even further, correlating data from multiple security layers including the network, cloud, and email. This holistic view enables security teams to detect threats faster and understand the full scope of an attack, making it an essential component of any modern network security best practices framework.
For instance, CrowdStrike's Falcon EDR platform was instrumental in identifying and attributing the 2016 DNC hack by analyzing attacker behavior on the endpoints. Similarly, organizations with robust EDR solutions were able to rapidly contain the NotPetya ransomware outbreak by automatically isolating infected machines before the malware could spread across the network.
How to Implement EDR/XDR
Deploying an EDR or XDR solution is a critical step in maturing your security posture. It provides the deep visibility needed to hunt for threats proactively and respond decisively when an incident occurs.
- Deploy Comprehensively: Install the EDR agent on all endpoints, including servers and remote workstations, not just office desktops. This ensures complete coverage and eliminates blind spots attackers could exploit.
- Configure Automated Responses: Set up rules to automatically isolate endpoints when a high-severity threat is detected. This immediate action can contain a breach in seconds, preventing widespread damage.
- Integrate with Your Security Stack: Connect your EDR/XDR platform with other security tools, such as your SIEM (Security Information and Event Management) system. This integration provides a unified view for more effective threat hunting and incident analysis.
- Train and Test: Ensure your security team is trained on the platform's investigation and threat-hunting features. Regularly test the system's effectiveness using adversary simulation tools like MITRE Caldera to validate configurations and response procedures.
By adopting EDR/XDR, businesses gain the ability to detect and neutralize advanced threats that would bypass legacy defenses, securing their most vulnerable assets.
10. Principle of Least Privilege and Access Control
Granting excessive access rights is like leaving every door in your building unlocked; it invites trouble. The Principle of Least Privilege (PoLP) is a foundational security concept that counters this risk by mandating that users, applications, and systems should only have the minimum access required to perform their specific, legitimate functions. It's a shift from a "trust by default" model to one of "access by necessity."
This best practice works by systematically limiting permissions, which dramatically reduces the potential attack surface. For example, the infamous 2013 Edward Snowden leak was possible due to excessive administrative privileges. If an attacker compromises an account with limited access, the damage they can inflict is contained. This principle is a cornerstone of robust network security, preventing both external attackers and insider threats from moving laterally to access sensitive data.
How to Implement Least Privilege
Adopting PoLP is a crucial step in maturing your security posture. It requires a diligent and ongoing effort to define, assign, and review permissions across your entire digital environment. To get a broader perspective on how this fits into a complete security strategy, it's helpful to understand what network security encompasses and its various layers.
- Identify and Document Privileges: Start by creating a comprehensive inventory of all user and service accounts, especially those with administrative or elevated rights. Document why each permission is necessary.
- Implement Role-Based Access Control (RBAC): Group users into roles based on their job functions (e.g., "Finance," "Marketing," "IT Admin"). Assign permissions to these roles rather than to individual users, ensuring consistency and simplifying management.
- Enforce Separation of Duties: Use separate, dedicated accounts for administrative tasks. A network administrator should use a standard user account for daily activities like email and only log into their privileged account when performing specific administrative duties.
- Conduct Regular Access Reviews: Schedule quarterly or semi-annual reviews of all user permissions. Remove orphaned accounts from former employees and strip away any privileges that are no longer required for a user's current role.
- Use Just-in-Time (JIT) Access: Implement systems that grant elevated permissions temporarily and for a specific purpose. This "just-in-time" access expires automatically, closing a potential vulnerability window.
By strictly adhering to the Principle of Least Privilege, businesses can significantly minimize their risk exposure, making it one of the most effective network security best practices available.
Network Security Best Practices Comparison Guide
| Security Measure | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Zero Trust Architecture | High – complex design, continuous verification | High – advanced tech, training, constant monitoring | Strong breach resistance; reduces lateral attacks | Organizations with dynamic perimeters, remote work | Minimizes attack surface; insider threat protection |
| Regular Security Patches and Updates | Moderate – scheduled, automated processes | Moderate – patch management tools, testing | Rapid vulnerability closure; compliance maintenance | All organizations seeking baseline security | Closes known vulnerabilities quickly; reduces malware risk |
| Multi-Factor Authentication (MFA) | Moderate – integration with systems, user setup | Low to moderate – software/hardware tokens | High account security; blocks automated compromises | Systems requiring strong authentication | Blocks 99.9% of automated attacks; low-cost security boost |
| Network Segmentation and Micro-segmentation | High – detailed network design and management | High – specialized skills and infrastructure | Limits breach impact; prevents attacker lateral movement | Environments with sensitive data and compliance needs | Contains breaches; improves traffic visibility |
| Strong Password Policies and Management | Low to moderate – policy setup and enforcement | Low – policies, password managers | Reduced brute force risks; unique credential usage | All organizations, especially those with many users | Encourages secure passwords; reduces reuse risks |
| Regular Security Awareness Training | Moderate – ongoing programs and simulations | Moderate – training platforms and time investment | Lower human error; improved incident reporting | Organizations aiming to reduce phishing and social engineering | Builds security culture; cost-effective defense |
| Backup and Disaster Recovery Planning | Moderate to High – backup setup and drills | Moderate to High – storage, bandwidth, testing | Data recovery; business continuity in disruption | All businesses with critical data | Enables ransomware recovery; reduces downtime |
| Continuous Security Monitoring & Incident Response | High – real-time alerting, SOC operations | High – tools, skilled personnel | Faster detection and response; threat visibility | Medium to large enterprises with security teams | Reduces breach impact; enables proactive defense |
| Endpoint Detection & Response (EDR/XDR) | High – deployment, tuning, integration | High – sophisticated software and analysts | Detects advanced endpoint threats; rapid incident handling | Organizations with diverse endpoint environments | Detects zero-day attacks; shortens attacker dwell time |
| Principle of Least Privilege & Access Control | Moderate to High – access audits, RBAC, PAM setup | Moderate – management tools, ongoing reviews | Limits privilege misuse; reduces insider threat risks | All organizations with complex access requirements | Minimizes attack surface; strengthens compliance |
From Theory to Action: Partnering for Proactive Security
Navigating the complex world of cybersecurity can feel like an overwhelming task, especially for small and mid-sized businesses where resources are often stretched thin. We've explored a comprehensive array of network security best practices, from establishing a Zero Trust Architecture and implementing Multi-Factor Authentication to the critical importance of regular employee training and robust backup strategies. Each of these ten pillars-including network segmentation, patch management, and continuous monitoring-represents a vital layer in a multi-faceted defense system.
Individually, these practices are powerful. Together, they form a cohesive, resilient shield against the relentless and evolving threats that define the modern digital landscape. The core takeaway is a fundamental shift in mindset: moving from a passive, reactive stance to a proactive, vigilant security posture. This isn't about simply installing software and hoping for the best; it's about building a living, breathing security culture that permeates every aspect of your organization.
The Challenge of Implementation
Understanding these concepts is the essential first step, but consistent, expert implementation is where the real value is realized. For a dental practice, a law firm, or a growing retail business, the daily demands of serving clients and managing operations leave little room for mastering the intricate details of Endpoint Detection and Response (EDR) or the nuances of the Principle of Least Privilege.
This is the gap where many organizations falter. A security strategy is only as strong as its weakest link, and that link is often a lack of time, specialized knowledge, or dedicated personnel.
Key Insight: Effective network security is not a one-time project; it is a continuous process of assessment, implementation, monitoring, and adaptation. Threats evolve daily, and your defenses must evolve with them.
Your Actionable Next Steps
To transform these network security best practices from a checklist into a tangible reality, consider these immediate actions:
- Conduct a Self-Assessment: Use the topics covered in this article as a scorecard. Where are you strong? Where are the glaring gaps? Be honest about what is currently implemented versus what is merely planned.
- Prioritize the High-Impact Items: You don’t have to do everything at once. Implementing Multi-Factor Authentication and creating a strong password policy are often quick wins that significantly boost your security posture.
- Engage Your Team: Security is a shared responsibility. Start the conversation about security awareness. Schedule your first official training session or send out a communication reinforcing the importance of vigilance against phishing.
- Seek Professional Guidance: Recognize that you don't have to be the expert in everything. Partnering with a managed IT services provider can offload the immense burden of security management, ensuring that best practices are not just understood but are expertly implemented and continuously maintained.
Ultimately, investing in a robust security framework is not just an operational expense; it is a strategic investment in business continuity, client trust, and long-term resilience. By embracing these principles, you protect your critical data, safeguard your reputation, and build a stronger, more secure foundation for future growth. Don't wait for a security incident to force your hand-take proactive control of your digital destiny today.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com



