Business Email Compromise (BEC) isn't about fancy malware or complex hacking tools. At its core, it’s a sophisticated con game—a digital version of a classic hustle that targets your employees to trick them into sending money or sensitive data directly to criminals.
The entire scam hinges on a simple but powerful premise: impersonating a trusted figure, like your company's CEO or a long-time vendor, to manipulate people into doing something they shouldn't.
What Is Business Email Compromise?
Think of a modern-day con artist who's done their homework on your business. They know who's in charge, they understand how you pay your bills, and they can craft an email that sounds exactly like someone you trust. That's the heart of Business Email Compromise. It's a crime that weaponizes trust itself.
Unlike a typical cyberattack that uses a virus to break in, BEC relies on social engineering. This is just a technical term for the psychological manipulation of people. The attacker's goal is to make a fraudulent request seem so believable and routine that your team fulfills it without a second thought.
The Human Element of BEC
What makes BEC so dangerous is its focus on exploiting human nature, not technology. Attackers know that a busy employee is less likely to question an "urgent" request from the boss or a demand from a supplier. It’s a shortcut that bypasses all your expensive firewalls and antivirus software.
They pull this off in a few common ways:
- Executive Impersonation: A scammer pretends to be your CEO or CFO and emails someone in the finance department. The message is always urgent and confidential, usually demanding a secret wire transfer for a "special project" or an emergency payment that can't wait.
- Invoice Fraud: This is a sneaky one. An attacker impersonates a familiar vendor and sends an invoice that looks almost identical to the real thing, except for one tiny detail: the bank account number has been changed. Your accounts payable team, seeing a bill they expect, might pay it without ever realizing the money is gone for good.
- Account Compromise: Sometimes, the attackers go a step further and gain access to a real employee's email account. From inside, they can lurk, read conversations, and wait for the perfect moment to redirect a legitimate payment or steal valuable information. This makes the fraud almost impossible to spot.
The financial damage from these scams is astronomical. Business Email Compromise is now the most costly form of cybercrime out there, causing a jaw-dropping $6.7 billion in losses worldwide. For small and mid-sized businesses, the fallout is often devastating, with average costs from a single incident hitting $487,000. You can dig deeper into these BEC statistics and their financial impact to see the full picture.
Ultimately, understanding what business email compromise is comes down to recognizing it's a crime of deception. It’s not about sophisticated code; it’s about a well-researched, carefully crafted lie aimed at the one vulnerability no software can patch: human trust.
How Scammers Pull Off a Business Email Compromise Attack
Think of a Business Email Compromise attack less like a smash-and-grab and more like a carefully planned heist. These aren't random, opportunistic emails. They are calculated operations where the criminals do their homework on your company, waiting for the perfect moment to strike.
The entire scam is built on a foundation of detailed reconnaissance. Long before you ever see a suspicious email, the attacker is studying your business from the outside, piecing together a map of your internal world.
- Your Website is Ground Zero: They'll pour over your "About Us" and "Meet the Team" pages, identifying who's who in finance, HR, and the C-suite. They're looking for the people with the authority to move money.
- LinkedIn is a Goldmine: Scammers love LinkedIn. It lets them figure out your company's hierarchy, job titles, and even the professional tone your key people use in their communications.
- Public Breadcrumbs: They'll scan press releases and news articles to learn about recent events—like a merger, a big new project, or a new partnership. They use these details to make their fraudulent requests sound incredibly timely and legitimate.
This isn't just about collecting names. It’s about understanding the relationships, the power dynamics, and the standard procedures that make your business tick.
The Attack Begins
Once they have a solid blueprint of your operations, the attacker moves in. This is where they put on their disguise and send the email designed to trick you. Their whole game is to look like someone you know and trust, and they usually do this in one of two ways:
- Email Spoofing: This is the art of forgery. An attacker might register a domain that’s just one character off from yours (like
accounting@yourcompnay.cominstead ofaccounting@yourcompany.com). Or, they might just change the "display name" to your CEO's name, betting you won't look closely at the actual email address it came from. - Email Account Compromise (EAC): This is the far more dangerous method. Here, the attacker has already gained access to a real employee's email account, usually through a separate phishing attack. They can sit inside that inbox for weeks, silently observing conversations, learning your company's lingo, and waiting for the perfect opportunity. When they finally make their move, the fraudulent request comes from a legitimate account, making it almost impossible to spot.
With their disguise in place, they send the email. It will almost always create a sense of urgency or secrecy, pressuring the recipient to act immediately without stopping to ask questions.
This diagram breaks down the simple, three-step flow of a typical BEC attack, showing how a scammer turns an employee into an unwitting accomplice.
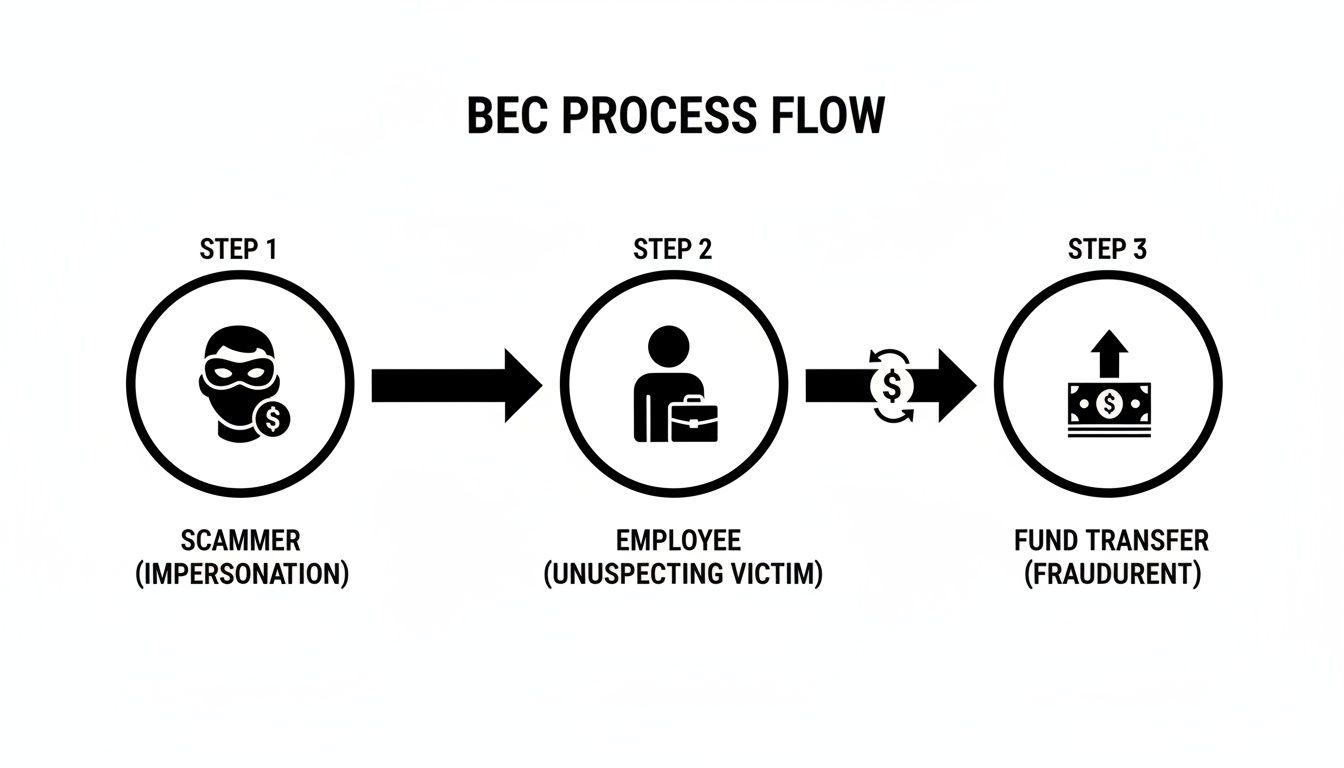
As you can see, the employee is the pivot point. Their awareness—or lack thereof—is what makes or breaks the entire scam.
Unpacking a Real-World Scenario
Let's imagine a busy dental practice that regularly works with a local law firm. The attacker has been watching. They know the practice manager is the one who pays all the bills and that the law firm is a trusted, routine vendor.
Here’s how the scam unfolds:
- The attacker spoofs an email address to look almost exactly like it's from their lawyer.
- They write an email impersonating a specific partner at the firm, mentioning a recent office expansion they read about in the local news. The context feels right.
- The email claims that due to a last-minute "internal bank audit," all future invoices must be paid to a new account. It provides new wiring instructions.
- To turn up the heat, the message stresses that the change needs to happen before 5 PM to avoid delaying the expansion project.
The practice manager, juggling a dozen other tasks, sees a familiar name and a request that makes sense. They quickly update the payment details in the system. Weeks later, the real invoice from the law firm arrives with a past-due notice. By then, the money sent to the scammer's account is long gone.
This is Business Email Compromise in a nutshell: a clever game of impersonation and psychological pressure.
The Game Has Changed: Today's BEC Threats Are Smarter and Scarier
Forget the old, clumsy phishing emails riddled with typos. Business Email Compromise attacks have seriously leveled up. The threats hitting your inbox today are polished, well-researched, and frighteningly convincing, making them incredibly difficult for even the sharpest employees to catch. This isn't about casting a wide net anymore; it's calculated, surgical deception.
Modern BEC attackers do their homework. They aren't just sending random, generic requests. They take the time to learn your company's structure, who the key players are, and how they communicate. They craft messages that feel perfectly normal, often referencing real projects or recent company events to create a powerful—and false—sense of legitimacy.

It’s Not Just About the CEO Anymore
While impersonating the boss is still a classic move, criminals have broadened their horizons. They are now frequently targeting employees in specific roles who have access to sensitive data or, more importantly, the ability to move money.
Think about these scenarios:
- Human Resources: An attacker, posing as a trusted employee, emails HR to "update" their direct deposit information—sending their paycheck straight to a fraudulent account.
- Payroll Departments: This is a similar play. Scammers target payroll staff to divert salary payments, sometimes for multiple employees at once.
- Executive Assistants: Tricking an assistant can be a goldmine. It can give an attacker access to calendars, contact lists, and confidential details they can use to launch even more believable secondary attacks.
This shift shows that attackers know the path of least resistance isn't always through the executive suite. They are now exploiting the everyday, routine processes that your business relies on.
The New Tools of the Trade: AI and Deepfakes
The next wave of BEC is already here, and it's powered by technology that makes impersonations almost perfect. Attackers are now using artificial intelligence and deepfake technology to take their scams to a whole new level.
The sheer speed and sophistication of these attacks are accelerating. Europe saw a staggering 123.8% increase in BEC attacks in April 2024 compared to the year before. The United States continues to be the primary target, with reported losses hitting $2.9 billion and the average loss per incident climbing to $137,000. You can find more detail on these BEC attack statistics and trends on hoxhunt.com.
AI-powered tools can now write flawless emails that perfectly mimic a specific person’s tone, vocabulary, and even their unique quirks. The tell-tale red flags that used to give away a fraudulent email are quickly disappearing.
What’s truly alarming is the rise of deepfake audio. With just a few seconds of audio—often scraped from a public video or podcast—a scammer can clone someone's voice. They then use this cloned voice in a phone call or voicemail to "personally confirm" a bogus wire transfer request. This adds a powerful layer of social proof that can fool even the most cautious employee.
In this rapidly evolving threat landscape, yesterday’s security awareness training just isn't enough. Protecting your business requires a modern, proactive strategy that prepares your team for the sophisticated attacks of today and whatever comes next.
How To Spot The Red Flags Of A BEC Attempt
Business Email Compromise (BEC) attacks slip past filters because they look like everyday emails. Yet the smallest inconsistency can give them away. Teaching your team to recognize these details turns them into a powerful defense.

Unlike spam or malware-laden messages, BEC scams rely purely on social engineering. That puts the onus on your people. Equip employees with the right know-how, and you cut the attackers’ chances.
The Devil Is In The Details
Attackers often swap a single character in an address—a tactic known as typosquatting. For instance, they’ll send a note from dave@gtcornputing.com instead of dave@gtcomputing.com. Busy minds tend to autopilot right past that tiny change.
They also might swap .com for .co or hide behind a familiar name on a free email account. Always hover over the display name to see the real sender address. A crucial skill for detecting sophisticated BEC attempts is learning how to read email headers to uncover digital clues that expose the true sender.
Psychological Pressure Points
Scammers shape their messages to push you into a corner. Be wary when you see:
- Urgency and Deadlines: Words like URGENT, “act now,” or “before end of day” are red flags. They short-circuit your ability to question the request.
- Secrecy Requests: “This is confidential” or “don’t mention it to anyone else” isolates you. Scammers know it stops you from seeking a second opinion.
- Odd Process Changes: A vendor asking you to send funds to a new account, or a CEO requesting a personal-wire transfer, are major anomalies. When procedures suddenly change without backup, alarm bells should ring.
If an email makes you feel rushed or uneasy, pause. Verify via a different channel—pick up the phone or stop by their desk.
Understanding these cues is only half the battle. You also need to know how to protect against phishing attacks, since BEC often starts with a compromised inbox.
Legitimate Request Vs BEC Attack What To Look For
Use the table below to quickly compare genuine internal messages with deceptive BEC attempts. Notice where normal procedures end and malicious tactics begin.
| Characteristic | Legitimate Email | BEC Email |
|---|---|---|
| Tone | Consistent with your company’s style guide. | Overly urgent or unusually formal/informal for the sender. |
| Request Type | Follows standard protocols and approval chains. | Skirts normal processes, often citing secrecy or an emergency. |
| Email Address | Clearly matches the official domain and format. | Slight misspellings, uses a public domain, or misleads with display name. |
| Verification | Easily confirmed by a quick call or chat. | Discourages any form of confirmation and insists on email-only replies. |
Seeing these side-by-side differences makes it easier to spot suspicious requests. When your team internalizes these checks, those tiny deceptions lose their power.
Building a Practical BEC Prevention Strategy
There’s no magic bullet for stopping Business Email Compromise. A truly strong defense is all about building a resilient security culture, one that’s supported by overlapping layers of protection. Think of it as a three-legged stool: the technology you use, the processes you follow, and the awareness of your people.
If one leg wobbles, the other two can keep things stable. By addressing all three areas, you create a robust system where a failure in one spot is caught by another. It's the most effective way to shield your business from the financial and reputational fallout of a successful BEC attack.
Fortifying Your Technical Defenses
Your first line of defense is using technology to automatically block or flag malicious emails before they ever land in an employee's inbox. These technical controls are the silent guardians working in the background to filter out the noise and reduce your overall risk.
Here's what you need in your toolbox:
- Multi-Factor Authentication (MFA): Honestly, this is the single most important step you can take. MFA requires a second proof of identity—like a code from a phone app—before granting access. Even if a scammer manages to steal an employee's password, MFA slams the door shut. To get a better handle on its power, you can learn more about what two-factor authentication is and how it works.
- Email Authentication Protocols: Sounds technical, but the concept is simple. Tools like DMARC, SPF, and DKIM act like a digital seal of approval, verifying that an email is actually from the sender it claims to be from. They make it incredibly difficult for attackers to spoof your company's domain or impersonate your vendors, stopping a huge chunk of fraudulent messages right away.
- Advanced Email Filtering: Old-school spam filters just don't cut it anymore. Modern security solutions use AI to analyze emails for subtle red flags—like unusual language, suspicious links, or signs of impersonation. They're designed to catch the sophisticated threats that would otherwise slip through.
Creating Bulletproof Processes
Technology alone isn’t enough. Scammers are experts at exploiting human nature and weak procedures. That's why strong, clear, and consistently enforced internal processes are so vital. The goal here is to weave verification steps directly into your daily operations.
The most critical process you can implement is out-of-band verification. It's a simple concept: confirm any sensitive request using a different communication channel.
If you get an email asking to change wire instructions or update banking details, don't just reply to confirm. Pick up the phone and call a number you know is legitimate for that person or company. A five-minute phone call can prevent a hundred-thousand-dollar disaster.
This one mandatory step short-circuits the entire scam. No matter how convincing the email looks, a quick call to a verified contact will expose the fraud on the spot.
Empowering Your People as a Human Firewall
At the end of the day, your employees are your last and best line of defense. A well-trained team that knows what to look for can spot threats that even the most advanced technology might miss. This isn't about a boring, once-a-year PowerPoint presentation; it requires ongoing security awareness.
Today’s BEC attacks are meticulously planned. Scammers study LinkedIn profiles, look up organizational charts, and craft highly specific, plausible requests. This level of sophistication requires a layered defense that combines technology like DMARC (which saw adoption jump from 43% to 54% in 2024), strict verification processes, and sharp employee training. You can read more about these evolving BEC tactics on vipre.com.
For training to actually stick, it needs to be:
- Continuous: Think regular, bite-sized refreshers and realistic phishing simulations. This keeps security top-of-mind all year round.
- Relevant: Focus on the real-world threats your team is likely to see. Accounting needs to know about invoice fraud, while HR should be on alert for W-2 scams.
- Empowering: You have to build a culture where people feel safe questioning a suspicious request, even if it seems to come from the CEO. They need to know they'll be praised for their caution, not punished for slowing things down.
By weaving together these technological, procedural, and human layers, you build a formidable defense that makes your business a much, much harder target for cybercriminals.
Your Incident Response Plan for a Suspected Attack
That sinking feeling when you realize a BEC attack might be underway is intense. It's easy to panic, but having a clear, rehearsed plan is the single best tool you have to shut the attack down and minimize the damage. What you do in the first few minutes can be the difference between a close call and a devastating financial loss.
This is no time to improvise. Your team needs a simple, step-by-step playbook to run the second someone suspects a threat. Every moment counts, so a coordinated, pre-planned response is absolutely essential.
Immediate Actions to Take
If an employee flags a suspicious email, your initial response should be muscle memory. There are three critical first steps to take to contain the threat before an attacker can do any more harm.
Follow this sequence without fail:
- Don't Engage. The most important rule is to do absolutely nothing with the email itself. Don't reply, don't click any links, and don't open any attachments. Any interaction confirms your email address is active and can give the attacker more information to work with.
- Alert Your IT Team. Immediately get in touch with your IT support or managed services provider. They need to analyze the email, check for any signs of a compromised account on your network, and start their own security procedures to lock things down.
- Verify "Out-of-Band." This is key. Use a completely different communication channel to check if the request is real. Pick up the phone and call a known, trusted number for the person or company who supposedly sent the email. A quick phone call will expose a scam in seconds.
Responding quickly is critical. One study found that over half of BEC victims were able to recover at least 82% of their stolen funds, but only when they reported the incident fast enough for banks and law enforcement to intervene.
Critical Follow-Up Steps
Once you've contained the immediate threat, the next phase is all about damage control and official reporting. If you discover a fraudulent transaction has already gone through, you need to act even faster.
First, contact your bank immediately and report the fraudulent transfer. Give them every detail you have and ask them to initiate a recall or freeze the funds. The sooner they know, the better your chances of getting the money back.
Next, report the incident to the authorities. The FBI's Internet Crime Complaint Center (IC3) is the right place to start. This not only helps with the investigation but also provides law enforcement with crucial data to track and dismantle these criminal networks. Having this kind of response framework is a core part of any effective small business disaster recovery plan that helps you bounce back from a crisis.
A Practical Approach to Protection
Protecting your business from email scams isn't just about installing the latest software. It's a combination of smart technology, solid internal processes, and good old-fashioned awareness.
Even with the best defenses, it's wise to have a financial backup plan. This is where things like cyber liability insurance for small businesses come in, acting as a crucial safety net if the worst happens.
Ultimately, having an IT expert in your corner helps ensure all these layers of defense work together, shielding your operations from these increasingly clever attacks.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
.



