So, what exactly is network security?
Think of it like the security system for your office building, but for your digital assets. It isn't just one lock on the front door. It’s a complete, layered strategy—combining reinforced doors (firewalls), security cameras (monitoring), access keycards (user permissions), and on-site guards (IT team)—all working together to protect what's inside.
Network security applies that same comprehensive approach to your digital world.
Your Digital Fortress: Understanding Network Security
At its heart, network security is all about preventing unauthorized access to your company's network. The real goal is to protect the usability, reliability, integrity, and safety of both your network and the data flowing through it. It’s not just one piece of software; it's a carefully planned mix of hardware, software, and company policies that create multiple layers of defense. If a threat gets past one layer, another one is waiting to stop it.
This protective strategy is non-negotiable because every modern business, whether it's a local accounting firm or a regional manufacturer, runs on data. Your client lists, financial records, and private communications are incredibly valuable assets that need to be defended.

The Core Goal: Protecting Your Data
How do you know if your security plan is actually effective? It all comes down to its ability to uphold three core principles, famously known as the CIA Triad. These three pillars are the absolute foundation of a secure digital environment.
As cyber threats become more common and sophisticated, the demand for solid protection has exploded. The global network security market was valued at USD 28.4 billion in 2023 and is on track to hit USD 117.72 billion by 2035. You can find more details about this incredible market growth over on Roots Analysis.
This massive growth underscores a simple truth for businesses today: investing in security isn't optional anymore. A single data breach can lead to crippling financial loss, permanent damage to your reputation, and costly operational downtime.
The Three Pillars of Network Security (CIA Triad)
To truly grasp network security, you need to understand the CIA Triad. This isn't about intelligence agencies; it's about Confidentiality, Integrity, and Availability. Every security measure you put in place is designed to support one or more of these principles.
| Principle | What It Protects | Example in Business |
|---|---|---|
| Confidentiality | Prevents unauthorized disclosure of information. Ensures privacy. | Encrypting customer payment details so only authorized personnel can view them. |
| Integrity | Ensures data is accurate, consistent, and trustworthy. | Using access controls to prevent an unauthorized employee from altering financial records. |
| Availability | Guarantees that systems and data are accessible to authorized users when needed. | Implementing redundant systems to ensure your website stays online during a hardware failure. |
Getting these three pillars right is the first step toward building your own digital fortress. Each one addresses a unique aspect of data protection, making sure your information remains safe, accurate, and accessible only to the right people, right when they need it.
The Building Blocks of Your Security System
Knowing the theory behind network security is one thing, but building a strong defense means putting the right tools in place. Think of these components as the specialized guards, cameras, and reinforced doors of your digital fortress. Each one has a specific job, and together, they create a layered defense that protects your business from all sides.
This infographic breaks down how core security tools like firewalls, antivirus software, and VPNs work in concert to build a solid security posture.
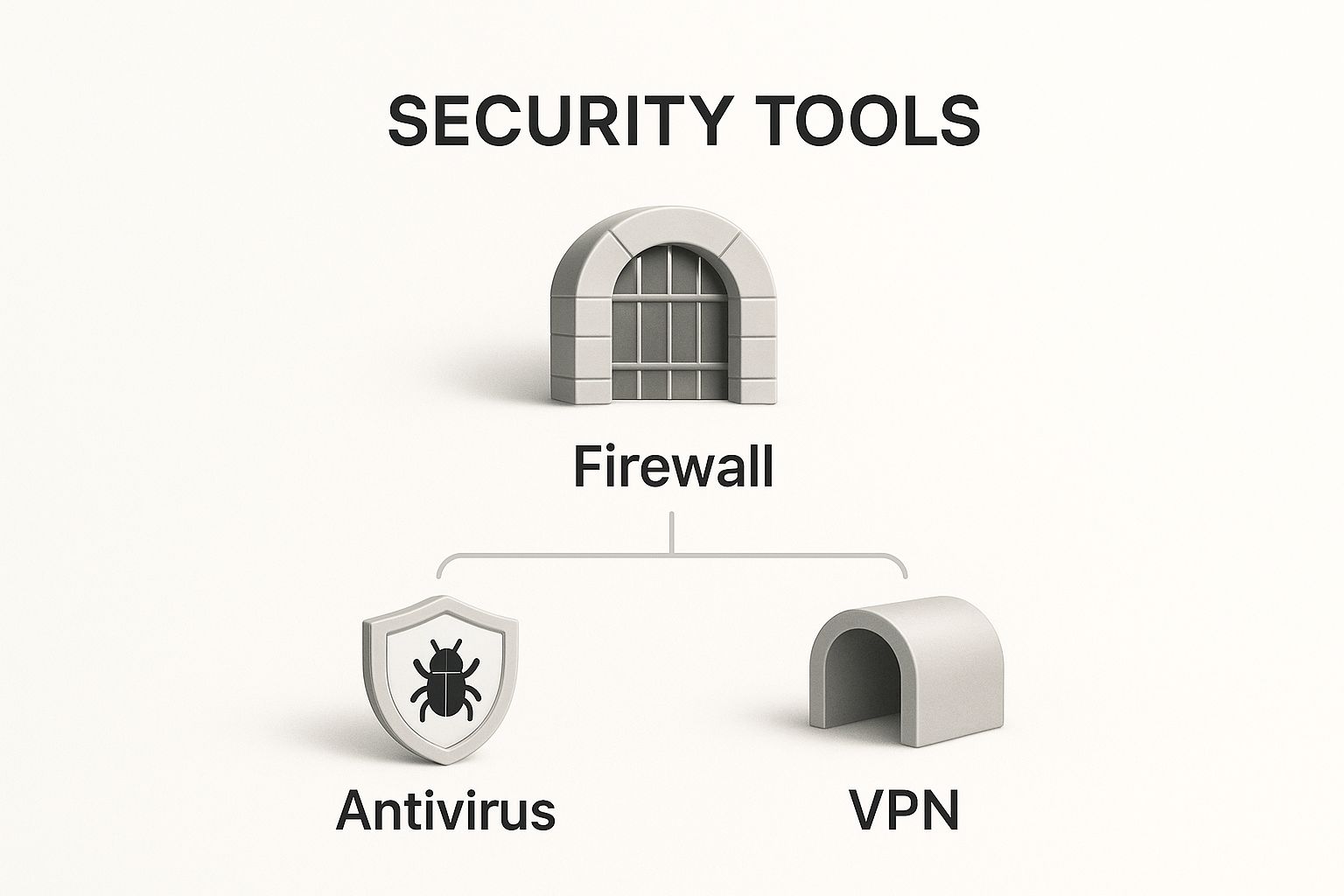
As you can see, a multi-layered approach is non-negotiable. No single tool can possibly defend against every threat out there.
Firewalls: The Digital Gatekeepers
The first line of defense for any network is its firewall. Picture it as a bouncer at the only door to your office. Their job is to check the ID of everyone and everything trying to get in or out, making sure they’re on the list.
A firewall does the exact same thing with your network traffic. It inspects all incoming and outgoing data packets, either allowing them through or blocking them based on a strict set of security rules you've defined. This simple but powerful function stops a massive number of unauthorized access attempts before they ever get close to your internal systems.
Antivirus and Anti-Malware: Your Network's Immune System
If the firewall is your bouncer, then antivirus and anti-malware software is your network's immune system. This software is constantly on patrol, actively scanning computers, servers, and other devices for known viruses, spyware, ransomware, and other malicious code.
Once a threat is spotted, the software jumps into action to quarantine and destroy it before it can spread and cause real damage. Modern antivirus tools get updated constantly with new threat signatures, which helps them identify and fight off even the newest strains of malware. Without this layer, a single infected email attachment could cripple your entire operation.
Virtual Private Networks (VPNs): Secure Tunnels for Your Data
With so many people working remotely, protecting company data as it travels across the public internet is more important than ever. That's where a Virtual Private Network (VPN) comes in. It creates a secure, encrypted "tunnel" for your data to travel through.
Think about an employee logging in from a coffee shop's public Wi-Fi. A VPN encrypts their connection, scrambling the data so it's completely unreadable to anyone trying to snoop on the network. This ensures sensitive company information stays private.
This technology is an absolute must-have for any business with employees who work from home, travel, or connect to company resources from outside the office.
Intrusion Prevention Systems (IPS): Your Active Surveillance Crew
While a firewall is great at blocking traffic based on preset rules, an Intrusion Prevention System (IPS) offers a more dynamic, active form of security. It’s less like a bouncer with a list and more like a high-tech surveillance team that doesn't just watch for trouble—it actively steps in to stop it.
An IPS constantly analyzes the flow of network traffic, looking for patterns that signal an attack in progress. If it spots suspicious activity, like a hacker trying to exploit a known software bug, it can instantly block the malicious traffic and send an alert. This proactive defense is a critical piece of the puzzle, and it works hand-in-hand with other strategies that keep you online, much like how businesses need to understand what is network redundancy to ensure their operations never grind to a halt.
Recognizing The Threats at Your Digital Doorstep
To build a solid defense, you first have to know what you’re defending against. Cyber threats aren't some far-off problem reserved for giant corporations; they are very real, everyday risks knocking on the digital door of businesses just like yours. Getting a handle on how these attacks work is the first real step toward stopping them.
The key is to look past the technical jargon and see these threats for what they are: direct assaults on your business's operations, finances, and hard-earned reputation. Let's walk through some of the most common ways criminals try to break in.
Phishing Scams: The Art of Deception
Phishing is one of the most common and dangerously effective attacks out there. Why? Because it doesn’t target your software; it targets your people. At its core, a phishing attack is a digital con game.
An attacker sends an email cleverly disguised to look like it's from a trusted source—a bank, a supplier, or maybe even your own CEO. These messages often create a false sense of urgency, pressuring an employee to click a malicious link or open an infected attachment. Once they take the bait, the attacker can snatch login details or plant harmful software on your network.
Ransomware: Your Data Held Hostage
Picture this: you walk into the office one morning to find every single file on your network locked, encrypted, and completely inaccessible. That’s the reality of a ransomware attack. This type of malicious software essentially takes your data hostage.
The criminals then demand a huge payment, typically in cryptocurrency, in exchange for the key to unlock your files. Paying the ransom is a massive gamble with zero guarantee you'll ever see your data again. But not paying could mean losing everything and grinding your business to a halt.
Ransomware is a particularly nasty threat because it directly paralyzes a business. For industries that rely on sensitive data, the fallout is even worse. The healthcare sector, for example, is a prime target because of its dependence on digital records and connected medical devices.
While the financial industry has always been a top target, healthcare is now the fastest-growing sector for network security needs, with a projected growth rate of 15.80% annually through 2030. This surge is driven by the desperate need to defend against disruptive attacks like ransomware. You can explore more market trends on Mordor Intelligence.
Common Threats and Their Business Impact
Understanding these threats is one thing, but seeing how they can directly impact your bottom line is another. Here’s a quick breakdown of common attacks and the damage they can do.
| Threat Type | How It Works | Potential Business Impact |
|---|---|---|
| Phishing | Deceptive emails trick employees into revealing credentials or downloading malware. | Data breaches, financial fraud, reputational damage, and loss of customer trust. |
| Ransomware | Malware encrypts all your files, and attackers demand a ransom for the decryption key. | Complete operational shutdown, catastrophic data loss, and significant financial costs. |
| Denial-of-Service (DoS) | Your website or server is flooded with junk traffic, overwhelming it and knocking it offline. | Lost sales, customer frustration, and damage to your brand's reliability. |
| Man-in-the-Middle (MitM) | An attacker secretly intercepts communications between two parties to steal data. | Theft of sensitive information like login details, credit card numbers, and trade secrets. |
As you can see, each threat carries a heavy price, making a proactive defense not just a good idea, but a business necessity.
Denial-of-Service (DoS) Attacks
A Denial-of-Service (DoS) attack has a much simpler, cruder goal: to knock your website or network offline. The attacker simply floods your server with so much junk traffic that it can no longer respond to legitimate requests from your actual customers.
For any business that depends on its website for sales or customer support, a DoS attack is a direct hit to your revenue and your customers' trust in you.
Man-in-the-Middle (MitM) Attacks
Think of a Man-in-the-Middle (MitM) attack as a form of digital eavesdropping. An attacker secretly places themselves between two communicating parties—say, your employee and the cloud application they're using—and intercepts everything.
This allows the criminal to steal sensitive data like login credentials or financial details in real time. The worst part? The victims often have no idea they’re being spied on until it's too late.
Putting Network Security Into Practice: Your Action Plan
Knowing the threats is one thing, but stopping them requires action. This is where we move from theory to reality. By putting a few core security habits in place, you can build a much stronger defense around your business and make life significantly harder for anyone trying to break in.

Don't worry, these aren't complex technical overhauls. They're the non-negotiable fundamentals that form the backbone of any solid security strategy. Let's walk through the most impactful steps you can take right now.
Fortify Your Front Door
Your access points—every password and login—are the low-hanging fruit for cybercriminals. Locking them down should be your top priority; it delivers the biggest security payoff for your effort.
Start by rolling out a strong password policy. This isn't just about length anymore. It means forcing the use of complex passphrases that blend uppercase and lowercase letters, numbers, and symbols. Even more important is enabling Multi-Factor Authentication (MFA) on every account that offers it. MFA adds a second layer of verification, like a code sent to a phone, which stops a criminal in their tracks even if they've stolen a password.
Think of MFA like needing both a keycard and a PIN to enter a secure room. A thief might swipe the keycard (the password), but without the constantly changing PIN (the MFA code), that door isn't opening.
Keep All Your Software Up to Date
Outdated software is riddled with security holes—think of them as unlocked windows in your office building. Hackers actively hunt for these vulnerabilities, while developers are in a constant race to release patches that seal them up. This is why consistent software updates and patch management are absolutely vital.
You need to regularly update everything connected to your network: operating systems, browsers, business software, and even the firmware on your routers and firewalls. Setting these updates to happen automatically is the best way to close security gaps the moment a fix is available. Of course, having the right protection is key, which is why we’ve created a guide on the best antivirus for small business to help you choose wisely.
Lock Down Your Wireless Networks
An unsecured Wi-Fi network is like leaving your front door wide open. It’s an open invitation for intruders to walk right in and snoop around.
- Change Default Credentials: The first thing you should do is change the factory-set admin username and password on your router.
- Use Strong Encryption: Always use WPA3 (or at least WPA2) encryption. This scrambles the data traveling over your Wi-Fi, making it unreadable to eavesdroppers.
- Create a Guest Network: Set up a separate, isolated Wi-Fi network for visitors. This simple step keeps their devices—and any potential threats they carry—completely separate from your core business network.
Back Up Everything, Always
No matter how robust your defenses are, you have to be prepared for a worst-case scenario. Regular, automated data backups are your ultimate safety net against a devastating ransomware attack, hardware failure, or even a simple human error.
Live by the 3-2-1 backup rule: keep at least three copies of your critical data, on two different types of storage media, with one of those copies stored securely off-site. This strategy ensures you can get back up and running with minimal damage. The growing threat landscape is why the United States network security market, valued at USD 5.3 billion, is projected to more than double to USD 11.6 billion by 2033. You can learn more about these network security market projections on imarcgroup.com.
Build a Human Firewall
Finally, never forget that technology is only one piece of the puzzle. Your employees can be your greatest weakness or your most powerful security asset. The difference comes down to ongoing security awareness training.
Train your team to recognize phishing emails, understand the importance of secure passwords, and know the risks of connecting to public Wi-Fi. An educated and alert team is far less likely to fall for a scam, effectively shutting down one of the most common ways attackers get in.
Why Professional IT Support Is a Smart Investment
Using strong passwords and keeping your software updated are great starting points, but they are just that—a start. The world of network security is always in motion, with clever new threats and attack strategies popping up what feels like every single day. For a growing business, trying to keep up with this on your own isn't just a headache; it's a huge gamble.
Going the DIY route almost always leaves security holes you don't even know are there. Without a specialist's eye, you might set up a firewall incorrectly, miss a crucial software patch, or fail to spot the quiet signs of an attack until the damage is done. Let's be honest: modern network security is a full-time job for experts.
Beyond Basics: Access to Advanced Tools and Expertise
This is where partnering with a professional IT provider completely changes the game. Think of it as trading a basic wrench set for a high-tech garage staffed by seasoned mechanics. Professionals bring enterprise-level tools that are typically way too expensive or complicated for a small business to handle on its own.
We're talking about advanced threat detection systems, automated software updates, and powerful security analysis platforms. But even more important than the tools is the team. You get access to experts whose entire job is to live and breathe cybersecurity, staying one step ahead of the bad guys. They know the ins and outs of compliance rules like HIPAA or PCI DSS, making sure your business avoids the massive fines that come with violations.
A professional IT team doesn't just put out fires—they prevent them from starting. Their mission is to anticipate threats, strengthen your defenses, and keep your business running securely and smoothly, day and night.
From Cost Center to Strategic Investment
It's easy to look at professional IT support as just another bill to pay, but that's a shortsighted view. It’s actually a strategic investment in keeping your business alive and kicking. The cost of a single data breach—when you add up downtime, recovery efforts, fines, and the hit to your reputation—can easily wipe out what you would have spent on years of professional IT support.
Consider this: 24/7 monitoring means suspicious activity is caught the second it happens, not the next morning. Expert guidance helps your security plan grow and adapt right alongside your business. By handing off these critical security tasks, you free up your team to focus on what you're actually in business to do: taking care of customers and growing your company. This proactive approach is the core of effective managed IT services for businesses, turning IT from a reactive cost into a true business advantage.
Ultimately, professional support isn't just about stopping bad things from happening. It's about enabling good things to happen, securely and without interruption.
Common Questions About Network Security
As a business owner, you've got enough on your plate without becoming a cybersecurity expert overnight. It's completely normal to have questions as you try to figure out the best way to protect your company's data. We've gathered some of the most common questions we hear from clients and broken them down with clear, straightforward answers.
Getting a handle on these key points is the first real step toward building a security plan that actually works for your business. Let's dig into what’s probably on your mind.
Can I Just Use a Standard Firewall and Antivirus?
A lot of business owners think a basic firewall and a good antivirus program are all they need. Maybe a decade ago, that was close to the truth. Today, that simple combination is dangerously out of date.
Think of it like this: your firewall is the locked front door to your office, and the antivirus is the alarm system. But what about a con artist who tricks your receptionist into buzzing them in (phishing)? Or what if a thief finds an unlocked window on the second floor (an unpatched software bug)? The threats we see now are designed to get around those basic front-door defenses.
A modern, effective security strategy needs a multi-layered approach. This means your firewall and antivirus work alongside other critical tools like email filtering, multi-factor authentication, regular data backups, and even employee security training. Each layer is there to stop a different kind of attack, so if one fails, another one is waiting to catch the threat.
Relying on just a firewall and antivirus is like leaving most of your doors and windows wide open to sophisticated ransomware and data theft.
How Much Does Network Security Cost?
There’s no single price tag for network security. The cost is a spectrum that really depends on your business's size, what kind of data you handle, and your overall risk level. The investment can be as low as a few hundred dollars a year for essential software, or it could be a more significant monthly fee for a fully managed security service.
For a small business just starting out, the initial costs might cover:
- Business-grade antivirus software: This is an absolute must-have.
- A professional firewall: Much more robust than the one built into your router.
- Cloud backup solutions: Your safety net for when things go wrong.
As your business grows—or if you handle sensitive information like customer credit cards or patient records—your security needs get more complex. This is where managed services often become the smartest financial decision. While the monthly fee is higher, it includes 24/7 monitoring, expert support, and access to advanced security tools that would cost a fortune to buy and manage yourself.
What Is the First Step I Should Take?
If you're feeling overwhelmed and don't know where to start, there's one incredibly powerful action you can take right now to immediately boost your security.
The single most effective first step is to enforce Multi-Factor Authentication (MFA) on every possible account. We're talking email, cloud storage, banking—anything and everything that offers it.
Stolen passwords are, by far, the most common way attackers get in. MFA stops them cold. Even if a cybercriminal steals an employee's password, they can't log in without that second code from the employee's phone. Turning on MFA is fast, easy, and usually free. It’s the quickest way to build a much stronger wall around your business today.
Ready to Shore Up Your Defenses?
Knowing what network security is all about is a great start, but it's the action you take that truly counts. Think of it this way: you wouldn't just read about locking your doors at night—you'd actually do it. The same principle applies here.
A solid security plan is what stands between your critical business data and those who want to steal it. It’s what keeps your operations running smoothly and, just as importantly, what keeps your customers' trust intact. In the world of cybersecurity, waiting is a gamble. Every delay is another window of opportunity for a potential attacker.
Don't wait for a crisis to force your hand. Start securing your digital foundation today.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
.



