When a ransomware attack hits, your first moves are everything. You need to act fast—decisively—with a clear focus on containment first and recovery second. The immediate goals are simple: disconnect infected systems from the network, isolate your critical infrastructure to stop the bleeding, and then confirm your backups are safe, offline, and ready to go. What you do in that first hour can drastically limit the damage and set you up for a successful comeback.
Your First Moves in a Ransomware Crisis
Seeing that ransom note for the first time is a gut-punch. Your first instinct might be to panic, but the decisions you make in these initial minutes are the most critical of the entire incident. The number one priority isn't recovery; it's aggressive containment.
I've seen it happen: a single compromised laptop, left connected to the network, can bring an entire company to its knees in a matter of hours. Your job is to stop the spread, create a safe zone, and give yourself room to breathe and plan. This is the bedrock of any solid incident response plan.
It all boils down to three core actions: disconnect, isolate, and verify.
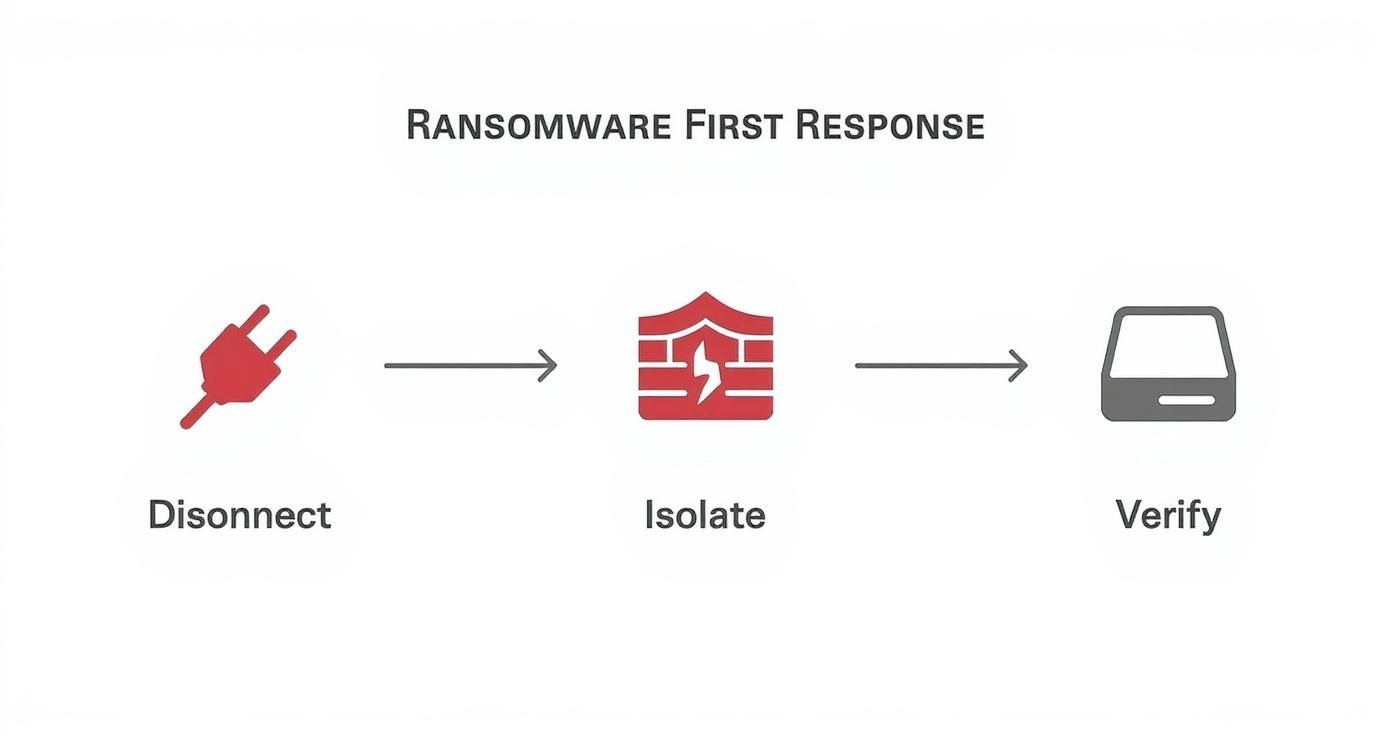
This process isn't just a suggestion; it's a lifeline. You have to contain the threat before you even think about anything else. After that, it's all about making sure your best recovery asset—your backups—is still viable.
When you're in the thick of it, having a simple checklist can be a lifesaver. It keeps the team focused and ensures no critical first steps are missed in the chaos.
Immediate Incident Response Checklist
| Action Item | Priority | Objective |
|---|---|---|
| Unplug Network Cables | Critical | Physically disconnect infected machines to halt lateral movement immediately. |
| Disable Wi-Fi/Bluetooth | Critical | Cut off all wireless communication paths for affected devices. |
| Segment the Network | High | Use firewalls/switches to quarantine the compromised network segment. |
| Take Backups Offline | High | Ensure backup systems are air-gapped or disconnected from the network. |
| Verify Backup Integrity | Medium | Check that backups are uncorrupted and scan them in a sandbox environment. |
| Document Everything | Ongoing | Start a timeline of events, actions taken, and systems affected. |
This checklist isn't exhaustive, but it covers the non-negotiable actions that must happen right away. Once these are underway, you can move into a more detailed analysis and recovery phase.
Disconnect and Isolate Immediately
Ransomware is engineered to spread. It's constantly hunting for network shares, mapped drives, and other endpoints to encrypt. That’s why your first physical action has to be pulling the plug. Literally. Unplug network cables from infected desktops and servers. For laptops and other wireless devices, disable Wi-Fi and Bluetooth immediately.
At the same time, someone needs to be working on isolating entire chunks of your network. If you can quickly pinpoint where the infection started, use your firewalls and network switches to block all traffic coming from or going to that segment. Think of it as creating a digital quarantine zone. This single action can prevent the malware from reaching your most critical assets, like domain controllers, backup servers, and other business-critical systems. The speed here is what separates a contained incident from a complete disaster.
"Isolating infected systems from the network both physically and logically is paramount. This prevents ransomware from spreading laterally to file shares, other endpoints, and backup targets. It's the digital equivalent of closing the fire doors during a blaze."
Secure and Verify Your Backups
While one part of your team is fighting the fire on the front lines, another group absolutely must turn its attention to your backups. Modern ransomware attackers are smart; they actively hunt for backup repositories to destroy them, taking away your ability to recover without paying. It is crucial to confirm that your backups are offline and truly "air-gapped"—physically disconnected and inaccessible from the live network.
Once you know your backups are safe from the ongoing attack, you have to verify them. Never assume they're clean. You have to inspect their integrity to make sure they haven't been corrupted or, worse, encrypted themselves.
Here's what to do:
- Confirm immutability: If you use immutable backups (and you should), check that they haven't been tampered with. These are designed to be unchangeable for a specific period, making them a powerful defense.
- Scan for malware: Before you even think about restoring, pull the backup data into an isolated "sandbox" environment and scan it thoroughly. The last thing you want is to restore your files only to re-introduce the ransomware.
- Check recent restore points: Work backward from the most recent backup to identify the last known good copy taken before the infection began. This will be your golden image for restoration.
Those first few hours are going to be chaotic and stressful, but these steps are non-negotiable. By having a clear plan to disconnect, isolate, and verify, you kill the attack's momentum and, most importantly, you hang onto your ability to recover.
Sizing Up the Attack and Identifying the Threat

You’ve pulled the plug and isolated the infected systems. The immediate chaos is contained, but now the real work begins. This is where the frantic pace of containment gives way to a careful, methodical investigation. Think of yourself as a crime scene investigator, piecing together exactly what happened and how bad the damage really is.
It's tempting to jump straight into restoring from backups, but that's a classic mistake that often leads to reinfection. Before you can even think about rebuilding, you need a crystal-clear picture of the damage. This means mapping out the scope of the attack, figuring out which ransomware strain you're dealing with, and analyzing the attackers' demands—all without ever contacting them.
Pinpointing the Scope of the Damage
First things first: you need a complete inventory of everything that’s been hit. This isn't a quick once-over. It's a detailed audit to figure out which systems, apps, and data are now encrypted. A single missed server or workstation can act as a beachhead for the malware to spread again, undoing all your hard work.
Start by cataloging every compromised device. You’re looking for the tell-tale signs: weird file extensions, ransom notes popping up on desktops, and critical applications that suddenly refuse to launch.
- Systems and Servers: Make a list of every single workstation and server (both physical and virtual) showing signs of compromise. Be sure to note their role—is it a critical file server, a domain controller, or a specific application server?
- Data and Databases: The real impact is often in what was encrypted, not just how much. Pinpoint exactly which file shares, databases, and other critical data stores are locked down.
- Cloud Assets: The attack might not be limited to your on-premise hardware. Scour your cloud environments for any signs of trouble. Check for encrypted files in cloud storage, compromised virtual machines, or odd behavior in any SaaS platforms connected to your network.
This detailed map is non-negotiable. It tells you which backups you need to pull, helps you prioritize what to restore first, and serves as critical evidence for both law enforcement and any potential insurance claims.
"A precise understanding of the attack's scope is essential. Without a full inventory of compromised systems and data, your recovery efforts are essentially blind. You risk restoring clean data onto a still-infected machine or missing a hidden backdoor left by the attackers."
Identifying the Ransomware Variant
Not all ransomware is created equal. Knowing the specific strain you're up against can dramatically change your options. Some older or sloppier variants have known weaknesses, and the security community has even released free decryption tools for them. It’s a long shot, but one worth taking.
The ransom note is your first clue. It often names the ransomware group or the specific malware. Also, look at the file extensions it's adding to your files (like .lockbit, .conti, or .ryuk). These are breadcrumbs.
Take those clues and head to online resources. A great place to start is the No More Ransom project. Their Crypto Sheriff tool lets you upload a sample encrypted file and the ransom note. If you get lucky, it will identify the strain and might even point you to a free decrypter.
Documenting Everything for Later
Throughout this entire process, act like every detail will be scrutinized later—because it will. Create a detailed timeline of events, from the moment you first suspected something was wrong to every single action your team takes.
Your incident log should be meticulous. Make sure it includes:
- Screenshots of ransom notes and examples of encrypted file directories.
- A complete list of every affected system, user account, and data repository.
- A safe copy of an encrypted file and the ransom note text to help with identification.
- Timestamps for every discovery and every action taken.
This isn't just bureaucratic busywork. This documentation is invaluable when you report the incident to authorities like the FBI's Internet Crime Complaint Center (IC3). It’s also the hard evidence your cyber insurance provider will need to process your claim. Solid proof of due diligence can make all the difference.
Getting the Infection Out of Your Network
After you've stopped the bleeding and isolated the infected machines, the urge to jump right into restoring your data is overwhelming. I've seen it time and time again—it’s the single biggest mistake you can make.
Pouring clean data back onto a dirty system is like trying to build a new house on a contaminated foundation. You're just setting yourself up for another disaster. Before you even think about restoring a single file, you have to create a completely sterile, trusted environment. That means hunting down and destroying every last trace of the ransomware, including any backdoors the attackers cleverly left behind.
The Great Debate: Wipe or Clean?
One of the first big calls you'll have to make is whether to try and "clean" an infected machine or just wipe it and start over. Cleaning seems quicker, but it's a massive gamble.
Think of it this way: ransomware is usually just the noisy finale. The attackers could have been quietly moving around your network for weeks, planting other nasty tools. Trying to surgically remove every piece of malware is incredibly difficult, and honestly, it almost never works. You can never be 100% sure you found every hidden file, every malicious registry key, or every scheduled task waiting to reinfect you.
That's why the consensus among security pros is clear: wipe and rebuild. Securely reformat the drives on every single machine that was touched—servers, desktops, even virtual machines. It’s the only way to get a truly clean slate.
Setting Up a "Clean Room"
You can't rebuild your systems on the infected network. You need what we call a "clean room"—a completely isolated recovery environment. This is a segregated part of your network, walled off from the compromised areas and disconnected from the internet, where you can safely rebuild everything.
Here's how to get one up and running:
- Cut It Off: Use a physical switch or dedicated firewall rules to create a network segment that is truly on an island. No traffic in or out.
- Bring in Trusted Tools: Only use verified, clean installation media and security software. I mean, go to a brand-new, completely uncompromised computer to download fresh OS installers, patches, and antivirus tools directly from the official vendors.
- Rebuild from Gold: Reinstall your operating systems from scratch using that trusted media. Don't even think about using old system images unless you are absolutely certain they were created long before the attackers first got in.
Restoring to a compromised system is the leading cause of reinfection. A patient, methodical approach to system wiping and rebuilding within an isolated "clean room" environment is the only way to break the cycle and ensure the attackers don't get a second chance.
This rebuilding phase is also the perfect time to start hardening your environment. As you bring each system back online, you should be tightening security configurations to make your network much tougher to crack next time.
Scan and Verify Before You Reconnect
Just because you reinstalled the operating system doesn't mean a machine is ready for primetime. Now comes the critical verification phase inside your clean room.
- Deploy and Update Security: The very first thing you should do is install a powerful endpoint protection tool. You can check out our guide on the best antivirus for small business for some solid options. Get it installed, update the definitions immediately, and then kick off a full, deep scan.
- Patch Everything: Before a system even gets a whiff of the live network, make sure every single security patch is applied. This closes the very doors the attackers likely walked through to get in.
- Watch It Closely: Let the newly built system run by itself for a while. Keep an eye out for any unusual network chatter, strange processes firing up, or weird file modifications. This is your last line of defense against something deeply embedded, like a rootkit that might have survived the wipe by hiding in the firmware.
Only after a machine has been rebuilt, patched, scanned, and monitored in complete isolation can you finally consider it "trusted." I know this process is slow and tedious, but skipping any of these steps is a recipe for getting hit all over again.
Bringing Your Data and Operations Back Online

After the painstaking work of containment and disinfection, you’ve finally reached the turning point. This is where all that careful preparation and disciplined crisis management starts to pay real dividends. The focus now pivots from defense to rebuilding as you begin the hands-on process of restoring data and breathing life back into your business.
This phase is far more than just dragging and dropping files from a backup drive; it's a strategic operation. You have to prioritize systems, meticulously verify data integrity, and ensure every move gets you closer to full operational capacity without accidentally reintroducing the threat. It's a delicate dance between speed and caution, and getting it right is everything.
Restoring From Your Secured Backups
Your backups are the linchpin of this entire recovery. Having secured and verified them earlier in the process, you can now start bringing that data home. How you go about this, however, really depends on the kind of backups you have and the systems you're rebuilding.
The first and most important rule of restoration: never restore directly into your old production environment. All of this work needs to happen inside the "clean room" you set up—that isolated network segment where you’ve been rebuilding wiped systems. This gives you a safe space to scan and validate the restored data one final time before it goes live.
You'll likely encounter a few common restoration scenarios:
- Full System Restore: For critical servers that were completely wiped, you'll be doing a bare-metal recovery. This means restoring the entire system image—OS, applications, and data—from a full backup.
- Virtual Machine Recovery: If you're running a virtualized environment, you can often restore entire VM snapshots or replicas. From experience, this is usually much faster than rebuilding a physical server from the ground up.
- Granular File Restore: For things like file servers or specific data shares, you might only need to restore the encrypted files themselves. This targeted approach can get key departments back up and running quickly while the bigger systems are still being worked on.
No matter the method, the playbook is the same: restore to the clean, isolated system, run comprehensive malware scans on the restored data, and only then do you even think about reconnecting it to the main network. A robust data backup and recovery plan is what separates a minor disruption from a company-killer.
"Restoring to a clean, isolated environment for verification is non-negotiable. It's the final quality control check that ensures you're not accidentally re-deploying the ransomware that was hiding dormant in a backup file."
Prioritizing What to Bring Back Online First
You can't restore everything at once. Trying to will just create chaos and drag out the outage. What you need is a prioritized restoration plan, and it has to be based on business impact. The goal is to get the most critical functions running first to stop the bleeding financially and operationally.
Get with your department heads and map out a tiered recovery list. It usually ends up looking something like this:
- Core Infrastructure: You have to start with the foundational services like domain controllers, DNS, and basic networking. Absolutely nothing else works without them.
- Mission-Critical Applications: Next up are the systems that make you money or are essential for your core operations. Think ERP systems, customer databases, or primary production software.
- Important Business Functions: Once the core systems are stable, you can move on to secondary but still vital functions, like your email servers and internal file shares.
- Individual Workstations: End-user machines are almost always last. Employees can often find ways to work with limited capacity while you're bringing the main systems back online.
The Big Question: Should You Pay the Ransom?
In the middle of all this technical work, the ransom demand is always looming. It can feel like a tempting shortcut to get out of this mess, but both the data and expert consensus paint a pretty bleak picture for those who pay. Paying the ransom isn't a guarantee; it's a massive gamble.
Restoring from your own backups is, by a huge margin, the preferred and more successful path. In fact, statistics show it's the most common method, used by 68% of victims. But the quality of those backups is critical. Organizations with uncompromised backups saw a 46% recovery rate within a week. For those whose backups were also hit by the attack? That number dropped to just 25%.
Paying is even riskier. While 56% of organizations paid a ransom, only 46% of them actually got their data back. And of the data they did get back, much of it was corrupted. You can dig into more of these ransomware statistics over on spacelift.io.
Paying doesn't just fail to guarantee recovery; it paints a target on your back, marking you as a willing customer for future attacks. It directly funds these criminal enterprises. The official recommendation from law enforcement like the FBI is crystal clear: do not pay. Focus your time and energy on a methodical, backup-driven recovery. It's more predictable, far more reliable, and it doesn't invite the bad guys back for round two.
Fortifying Your Defenses After the Attack

Getting your systems back online after a ransomware attack feels like crossing the finish line, but in reality, it's just the start of the next critical race. Surviving an attack gives you a painful but incredibly valuable opportunity to harden your defenses. This is your chance to turn a crisis into a catalyst for a much stronger, more resilient security posture.
The first step is a no-holds-barred post-mortem. You have to dig deep and get real answers to some tough questions. How, exactly, did the attackers get in? Was it an unpatched server, a stolen password, or a clever phishing email that someone clicked? This isn't about pointing fingers—it's about finding the cracks in your armor so you can seal them for good.
Building a Battle-Hardened Fortification Plan
The findings from your post-mortem are now the blueprint for your new defense strategy. This isn't the time for small tweaks. It’s time for meaningful upgrades that address the root cause of the breach and transform hard-won lessons into real-world protection.
Your plan should focus on creating a layered defense that makes an attacker’s job significantly harder.
- Go Beyond Basic Antivirus: If you're still relying on traditional antivirus, it's time to upgrade. Modern threats require an Endpoint Detection and Response (EDR) solution. These tools don't just look for known malware; they monitor system behavior to spot and stop the suspicious activities that signal an attack in progress.
- Get Aggressive with Patching: The odds are high that the attackers exploited a known vulnerability. You need to implement a strict, non-negotiable patch management policy. Critical security updates for operating systems, applications, and firmware can't wait weeks—they need to be applied immediately.
- Segment Your Network: If ransomware spread through your network like wildfire, it’s a clear sign your network is too flat. Use VLANs and internal firewalls to break it into smaller, isolated zones. This tactic, known as network segmentation, contains any future breach and prevents it from reaching your most critical servers and data.
Refining Your Backup and Recovery Strategy
Your backups were your lifeline, but there's always room for improvement. It's time to fully embrace the gold standard of data protection: the 3-2-1 rule.
The 3-2-1 backup rule is a simple yet powerful framework for resilience. It means you must have three copies of your data, store them on two different types of media, and keep one copy completely off-site and air-gapped.
An air-gapped or immutable backup is absolutely non-negotiable. This is a copy that is either physically disconnected from your network or is technologically unchangeable. Attackers can't encrypt what they can't reach, and this single step is one of the most effective ways to guarantee you can recover.
Don't Forget the Human Element
Technology alone can't solve this problem. Many ransomware attacks start with a simple human error, like an employee falling for a phishing email. This is why ongoing security awareness training is so vital.
Start running regular, mandatory phishing simulations for your entire team. These controlled tests are fantastic for training employees to recognize and report suspicious emails, turning what was once your biggest vulnerability into your first line of defense. The goal isn't to trick people; it's to build a healthy, instinctive skepticism.
Beyond training, we have to acknowledge the immense pressure this puts on our IT and security teams. The human toll of a ransomware incident is staggering: 41% of IT and security teams report increased stress and anxiety, while 31% suffer staff absences due to the pressure. What’s more, 25% of organizations replace their IT or security leadership after an attack. You can find more of these sobering statistics on the human consequences of ransomware over at BrightDefense.
Supporting your team through this is a core leadership responsibility. Give them the time, resources, and encouragement they need to recover, both professionally and personally. Their well-being is directly tied to your organization's security—a burnt-out, exhausted team can't possibly defend against the next threat.
Answering Your Ransomware Recovery Questions
When you're in the thick of a ransomware attack, you're under a mountain of pressure. Every decision feels critical, and the clock is ticking. Let's cut through the chaos and tackle the most urgent questions that come up during recovery.
Getting a handle on the situation is the first step. With clear answers, you can shift from just reacting to building a real strategy for getting back on your feet.
Should We Ever Pay the Ransom?
This is the million-dollar question, and often the first one asked. The urge to just pay and make it all go away is strong, but I can tell you from experience and from what all the data shows: do not pay the ransom.
Paying is a massive gamble, not a solution. There’s no guarantee the decryption key you get will even work. I’ve seen cases where companies paid up only to find the "recovered" data was hopelessly corrupt. Even worse, paying marks you as a willing target. It tells criminals you're good for the money, putting a giant bullseye on your back for them—or other groups—to hit you again.
Official guidance from the FBI and other law enforcement agencies is crystal clear: don't pay. That money goes directly into the pockets of criminal organizations, funding their next attack.
How Long Does Ransomware Recovery Take?
There's no single, easy answer here. A full recovery is almost never a quick fix. You could be looking at a few days or several weeks—it all depends on how widespread the attack was and how prepared you were for it. Industry reports show the average recovery time is now over 24 days.
What makes the difference? A few things really move the needle:
- Your Backups: Are they truly offline (air-gapped) and unchangeable? Having clean, tested backups is the single biggest factor in speeding things up.
- The Damage Done: Did they just hit a few laptops, or did they get into your core servers and domain controllers? The scope is everything.
- Your Team's Readiness: Do you have an incident response plan you've actually practiced? A team that knows the playbook will always be faster.
A well-rehearsed recovery plan is your best tool for shortening downtime. Organizations that regularly test their backup restoration processes are consistently able to get back online faster than those who are figuring it out on the fly.
Who Are the First Experts We Should Call?
Don't try to go it alone. As soon as you confirm an attack, you need to bring in the specialists.
- IT Security and Incident Response Firm: Get a third-party firm on the line. These folks live and breathe ransomware. They’ll handle the forensics, help you contain the damage, and guide your internal team through eradication.
- Legal Counsel: Call your lawyer, ideally one who specializes in cybersecurity incidents. They’ll navigate the tricky waters of regulatory notifications and data breach laws.
- Cyber Insurance Provider: If you have a policy, contact your provider right away. They have their own set of procedures you have to follow and can often connect you with trusted vendors for response and recovery.
Even with the rise in attacks, a good number of businesses have refused to pay, relying instead on solid incident response plans and backups to get their data back. Remember, the cost isn't just the ransom; things like downtime and damage to your reputation often end up being far more expensive. You can find more insights about the true cost of ransomware on Mimecast.com.
Keep Your Business Running, Minus the IT Headaches
At GT Computing, we know that technology should work for you, not the other way around. We offer fast, reliable IT support for both homes and businesses, covering everything from network setups to critical data recovery.
Our goal is simple: keep you secure, productive, and focused on what matters most. Whether you need a one-time fix or ongoing managed IT services, we're here to help.
Let's talk about what you need.
Contact us today for a free, no-obligation consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com



