For modern law firms, strategic IT solutions aren't just a line item in the budget—they're a core part of the business. This isn't about having the latest gadgets; it's a specialized suite of services designed specifically for the legal industry's unique and demanding environment. We're talking about everything from fortified cybersecurity and compliant cloud storage to a rock-solid network infrastructure.
Why Modern Law Firms Need Strategic IT
In the legal world, information is everything. It's the bedrock of client trust, the blueprint for case strategy, and the foundation of your firm's reputation. Today's law practices are under immense pressure to perform. Clients expect instant, secure communication, while regulatory bodies demand strict adherence to complex rules about how you handle data.

A generic, one-size-fits-all IT provider just won't cut it. That's like using a standard padlock to guard a bank vault. Your firm’s sensitive data—case files, privileged communications, financial records—demands a dedicated, multi-layered security system, not just a simple lock.
The Pillars of Legal IT
A proper IT strategy is the complete security system for that vault. It includes the reinforced walls, the 24/7 surveillance, and the strict access protocols needed to protect your firm's most valuable assets. This comprehensive approach is built on several key pillars that work together to keep you secure and efficient.
Think of it like this:
- Secure Infrastructure: This is the digital version of your office building. It includes the servers, networks, and individual computers that must be stable and protected from the ground up.
- Advanced Cybersecurity: This is your active defense system. It’s about proactive measures like firewalls, endpoint protection, and—crucially—employee training to defend against ever-present threats like ransomware and phishing attacks.
- Compliant Data Management: You need systems in place to manage, store, and access documents in a way that meets your ethical duties and legal requirements, whether that's HIPAA or specific ABA guidelines.
- Business Continuity: This is your emergency plan. It ensures your firm can keep operating with minimal disruption after a disaster, whether it's a simple server failure or something much bigger.
A well-architected IT environment does more than just prevent problems. It creates a competitive advantage, enabling faster case resolution, better client service, and unshakable confidence in your firm's ability to protect sensitive information.
Beyond Defense: A Strategic Advantage
Ultimately, investing in specialized IT for your law firm is about more than just playing defense. It's a strategic move to build a more resilient, efficient, and competitive practice. When you safeguard client data, you reinforce the trust that is the absolute bedrock of your profession.
By implementing streamlined systems for document management and collaboration, you empower your attorneys to work more effectively. They can focus on high-value legal work instead of wrestling with clunky technology. A true IT partner understands these nuances and can turn technology from a potential liability into a powerful asset that fuels growth and protects your firm's integrity.
Building Your Firm’s Digital Foundation
Your law firm's network infrastructure is the absolute bedrock of its technology. Think of it as the digital foundation everything else is built on. A shaky network doesn't just mean frustrating slowdowns; it can create critical vulnerabilities, leaving your most sensitive client data exposed. If you want to get IT solutions for law firms right, you have to start here.

It helps to picture your firm's network like the physical courthouse itself. It’s not just one single thing, but a whole collection of interconnected systems that have to work together perfectly to keep things secure and efficient. Each piece of the puzzle plays a very specific role in protecting the integrity of your practice.
The Courthouse Analogy for Your Network
When you visualize your network this way, the importance of each part becomes crystal clear. A weakness in any single area can compromise the entire structure, putting client confidentiality and your firm’s operations at serious risk.
- The Firewall as Your Security Checkpoint: This is the main entrance to your digital courthouse. It inspects all incoming and outgoing data, acting like a vigilant security guard that stops unauthorized access and malicious threats before they ever get inside.
- Servers as Secure Evidence Rooms: This is where your firm’s most critical data lives, from case files to financial records. Just like a real evidence room, your servers must be highly secure, properly cooled, and accessible only to authorized personnel.
- Network Cables and Wi-Fi as Private Hallways: These are the corridors connecting different chambers and offices. They need to be fast and secure, ensuring information travels quickly between your team members without any risk of being intercepted along the way.
Just as a courthouse requires robust physical security to function, your law firm requires a robust digital infrastructure. Neglecting this foundation is like leaving the courthouse doors unlocked overnight—it invites disaster.
Essential Components of a Modern Legal Network
To build this digital courthouse correctly, several key components are simply non-negotiable. Trying to get by with consumer-grade equipment from a big-box store just won't cut it for the security and performance demands of a modern legal practice. A professional setup is essential.
This means investing in business-grade hardware designed from the ground up for reliability and security. These components all work together to prevent bottlenecks and protect against cyber threats. After all, a slow network can absolutely cripple productivity, turning simple tasks like uploading discovery documents into a time-consuming nightmare.
A secure and stable network includes:
- Business-Grade Routers and Switches: These are the traffic directors of your network, managing the flow of data efficiently and securely between all your devices.
- High-Speed, Reliable Internet: A fast and stable connection is the lifeline of your firm. It ensures quick access to cloud services, legal research databases, and virtual court appearances.
- Secure Wi-Fi with Guest Access: Your main Wi-Fi network must be encrypted and locked down. A separate, isolated guest network can provide internet access to clients without giving them a backdoor into your sensitive internal systems.
Ultimately, your network is the central nervous system of your firm. It supports everything from your document management system to your cybersecurity defenses. Building a strong, scalable, and secure network isn't just an IT project; it's a fundamental business investment that underpins every other aspect of your practice, ensuring you can serve your clients effectively and securely for years to come.
A Modern Cybersecurity Defense for Law Firms
Protecting your firm's digital assets isn't about buying a single piece of software and calling it a day. It’s about building a multi-layered strategy, a concept we in the IT world call "defense in depth."
Think of your firm like a medieval castle holding priceless treasure—your client data. You wouldn't just build one wall and hope for the best. You'd dig a moat, build thick outer walls, station guards on the battlements, and have locked vaults for the crown jewels. Each layer makes an attacker's job harder.
This is critical because cyber threats aren't just a possibility; they're a constant, active risk for every law firm. A single successful attack can mean devastating data loss, steep regulatory fines, and a hit to your reputation that's almost impossible to recover from. We've seen ransomware attacks cripple unprepared firms, locking away essential case files and demanding huge sums.
Building Your Digital Fortress, Layer by Layer
A solid security plan tackles threats from every possible angle. Each layer has a specific job, and they all work together to create a barrier that’s incredibly tough to break. The goal is to make breaching your firm so difficult and time-consuming that attackers simply give up and look for an easier target.
Your first layers of defense are all about stopping obvious, external attacks before they even get close to your staff.
- Firewalls and Email Security: These are your castle's outer walls and moat. A professionally configured firewall acts as a gatekeeper, inspecting all traffic coming in and out of your network and blocking anything malicious. Advanced email security does the same for your inbox, filtering out spam, viruses, and phishing attempts—the modern-day spies trying to trick their way past the guards.
Patrolling the Battlements with Endpoint Security
Even the strongest outer walls can be bypassed. That’s why your next layer has to focus on protecting the individual devices your team uses every day—laptops, desktops, and mobile phones. In IT, we call these "endpoints," and each one is a potential door into your network.
This is where Endpoint Detection and Response (EDR) software comes in. Think of it as the vigilant guards patrolling the castle walls. Unlike old-school antivirus that just looks for known bad guys, EDR actively watches for suspicious behavior. If it sees a program trying to encrypt files without permission, it can instantly quarantine that device to stop the threat from spreading.
This infographic shows just how these different layers come together to build a much stronger defense.
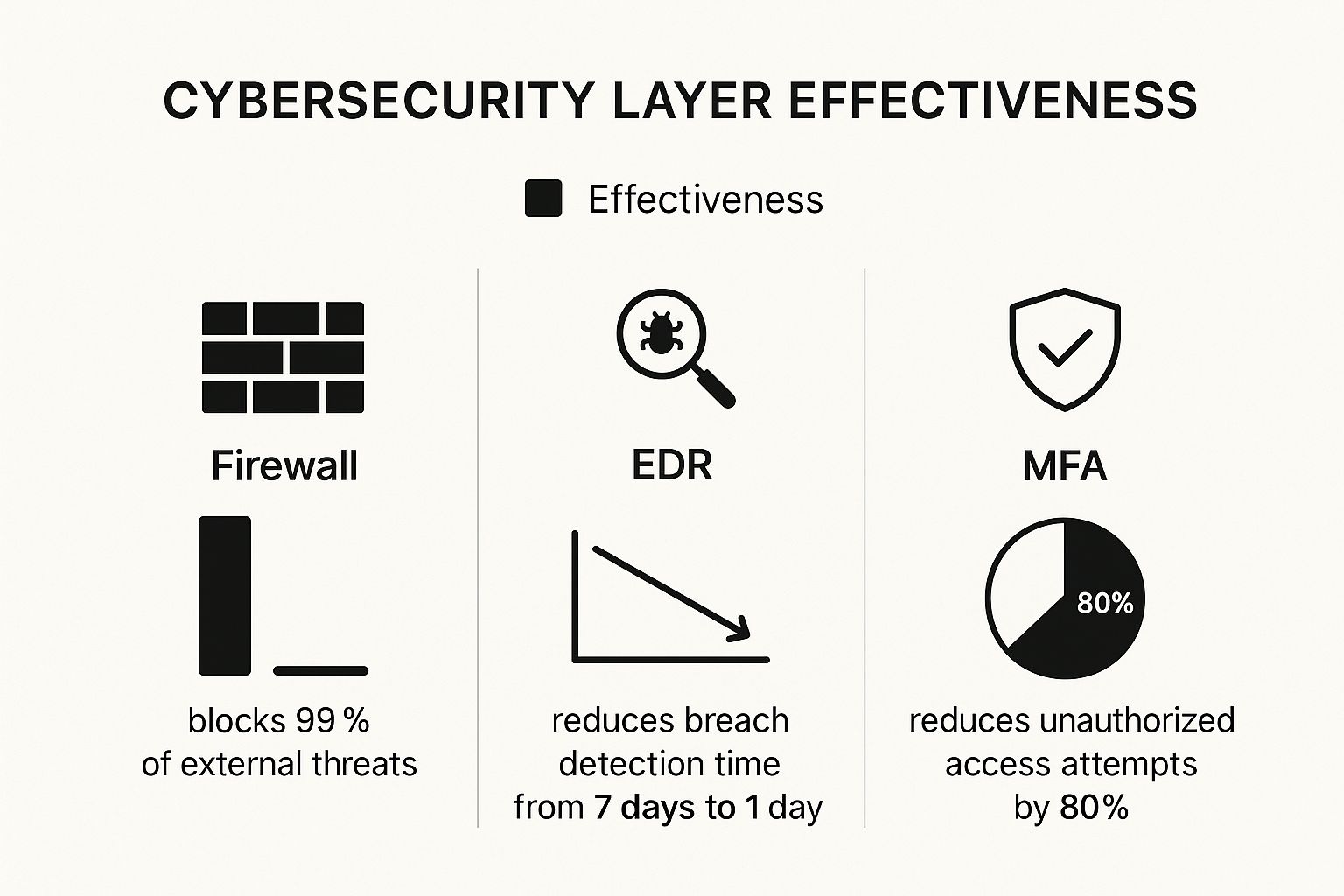
The data doesn't lie—a strategy with multiple layers is exponentially more effective than just relying on one tool.
Guarding the Crown Jewels with Strong Access Control
Now, what if an attacker makes it inside the castle walls? You need strong internal controls to keep them out of your most sensitive areas. This is where managing who can access what becomes so important. Not everyone on your team needs access to every single file.
Multi-Factor Authentication (MFA) is like the secret password needed to get into the king's private chambers. It forces users to provide at least two pieces of proof—usually their password and a code from their phone—before it grants access. This one simple step is one of the most powerful ways to stop unauthorized access, even if an employee's password gets stolen.
The Human Element: Your Most Important Defense
At the end of the day, your people are a critical line of defense. Hackers know this, which is why they love phishing attacks—deceptive emails designed to trick someone into giving up their login details or downloading malware. These are the spies trying to talk their way into the castle.
This is why security awareness training is completely non-negotiable. Regular training teaches your entire team how to spot and report suspicious emails, use strong passwords, and avoid common security mistakes. A well-trained team can spot a threat that technology might miss, turning a potential weakness into your strongest asset. To learn more about building a robust security posture, check out our detailed guide on cybersecurity services.
The legal industry is adopting new tech faster than ever, but that progress creates new risks. While 80% of law firms have adopted AI, data privacy is a huge concern. Cybersecurity is now the top IT priority for 37% of firms, but here's the problem: only 12% are actually spending what's needed on it. That creates a dangerous gap between knowing the risk and doing something about it.
Cybersecurity isn't a one-and-done project. It's a constant process of vigilance, adaptation, and training.
Choosing the Right Cloud and Document Systems
Moving your firm away from old-school, on-premise servers and into the cloud is one of the single most impactful IT decisions you can make. While the transition might seem daunting, the idea is actually quite simple. Don't think of "the cloud" as some mysterious, far-off place; picture it as a highly secure, shared digital library that your team can access from anywhere with an internet connection.
This is a complete departure from the days of physical filing rooms or a noisy server closet that chains your critical data to one physical location. Adopting cloud solutions brings immediate, real-world benefits that will make your firm more efficient and resilient.
Practical Benefits of Cloud Adoption
When you move your firm’s data and software to the cloud, you’re doing a lot more than just saving files online. It’s a fundamental shift in how your firm operates, freeing up valuable resources and improving your ability to serve clients effectively.
Here are a few of the key advantages:
- Reduced Hardware Costs: Forget about buying, maintaining, and eventually replacing those expensive on-site servers. You can trade a huge capital expense for a predictable, manageable operational cost.
- Seamless Case Collaboration: Your attorneys, paralegals, and even clients can securely view and work on case files in real-time, whether they’re in the office, at the courthouse, or working from home.
- Powerful Disaster Recovery: Cloud providers have built-in backup and redundancy systems that are far more robust than what a single firm could ever afford. This keeps your data safe from local disasters like fires, floods, or hardware failure.
By moving to the cloud, you're not just storing files online. You're adopting a more flexible, secure, and cost-effective operational model that allows your firm to adapt and grow.
Why Legal-Specific Document Management is Crucial
While general cloud storage like Dropbox or Google Drive is fine for personal photos and documents, law firms operate under a different set of rules. You need a specialized tool—a Document Management System (DMS)—built specifically for the legal industry. A legal DMS is designed from the ground up to handle the unique compliance, ethical, and workflow demands of a modern practice.
These platforms offer critical features that generic storage just can’t provide. For example, version control ensures you’re always looking at the most current draft of a motion or contract, while audit trails give you a detailed log of who accessed or changed a file and when—a lifesaver for compliance and defending against malpractice claims.
Even better, a legal DMS lets you create ethical walls to digitally separate information and prevent conflicts of interest between different cases. This is a fundamental requirement for professional conduct that’s nearly impossible to manage properly with basic folder permissions. To get a better handle on setting this up, check out our guide on securing file sharing in Microsoft SharePoint.
A Tale of Two Law Firms
Imagine a partner needs a crucial exhibit for a deposition that starts in ten minutes. At Firm A, which uses a messy shared server, a paralegal is frantically clicking through nested folders with names like "Client Docs_Final_v2." Billable hours are ticking away, stress levels are through the roof, and the document is found with seconds to spare—if it's found at all.
Now, picture Firm B, which uses a legal DMS. The paralegal types the case number and a keyword into the search bar. The exact document pops up instantly, complete with its full revision history. That’s the difference a purpose-built system makes. It turns a high-stress emergency into a routine, efficient task.
Comparing Cloud Storage vs Legal Document Management Systems
It's easy to see why a generic tool falls short when you compare them side-by-side. While both offer cloud access, a legal DMS is built for the specific, high-stakes work that law firms do.
| Feature | General Cloud Storage (e.g., Dropbox) | Legal DMS (e.g., Clio, NetDocuments) |
|---|---|---|
| Search Functionality | Basic keyword search, often limited to file names. | Advanced, metadata-based search (by case, client, document type, date). |
| Version Control | Simple version history, can be confusing. | Robust, automated version tracking and easy comparison of drafts. |
| Compliance Tools | Lacks specific legal compliance features. | Built-in audit trails, ethical walls, and retention policy management. |
| Integration | Limited integration with legal practice management software. | Deep integration with billing, time tracking, and e-discovery tools. |
| Security | General security measures. | Industry-specific security, encryption, and access controls for PII. |
| Ethical Walls | Not a standard feature; requires complex manual setup. | Built-in functionality to prevent conflicts of interest. |
Ultimately, relying on general cloud storage is like using a family car for a Formula 1 race—it might get you around the block, but it’s not designed for high performance or the specific rules of the track.
Staying Compliant and Keeping the Doors Open
In the legal world, two duties stand above all others: protecting your client's data and never letting them down. This is where regulatory compliance and business continuity come into play. These aren't just boxes to check; they're the very foundation of the client trust you work so hard to build.
Rules like HIPAA for healthcare law or the ABA's rules on tech competence aren't just suggestions—they set the bar for how a modern firm must operate. They lay out exactly how you need to handle sensitive information. Meeting these standards is a non-negotiable part of the job, and solid IT solutions for law firms are how you get it done.
Turning Compliance Rules into Real-World Action
Having a compliance policy sitting in a binder on a shelf does nothing. Real compliance requires active, technical controls that protect your data around the clock. Think of it less like a "Keep Out" sign and more like a state-of-the-art security system with motion sensors and alarms.
To meet these tough standards, your IT strategy needs to have a few key safeguards baked in:
- Data Encryption: This is the digital equivalent of shredding a document before you throw it away, only much more powerful. It scrambles your data so that even if a hacker gets it, it's just gibberish without a specific key. This applies to files on your server ("at rest") and emails or files you send over the internet ("in transit").
- Access Control Audits: You need to know exactly who can see what. This means running regular checks to ensure former employees can't log in and current staff only have access to the files they absolutely need for their work.
- Secure Data Archiving: This involves setting up smart, automated rules to either keep or securely destroy documents based on legal requirements. It stops accidental data leaks and makes things much easier if you ever face an e-discovery request.
Compliance isn't a one-and-done project. It’s an ongoing process. You have to stay on top of new rules and new threats to keep your firm ethically sound and legally protected.
From Disaster Recovery to True Business Continuity
Beyond the rules, you have to be ready for when things go wrong. What’s the plan if your server gives up the ghost, a ransomware attack locks down every single file, or a burst pipe floods your office? This is where disaster recovery and business continuity save the day.
Disaster recovery is the technical side—it's all about getting your data back. But business continuity is the big picture: How does your firm keep working and serving clients through the crisis?
Picture this: a critical server fails overnight. Firm A has no plan. They spend three days waiting for a technician to maybe fix the problem. In the meantime, they can't work, they miss deadlines, and their clients are getting angry. The firm is dead in the water.
Firm B, on the other hand, has a tested business continuity plan. Their IT partner gets an automatic alert the second the server goes down. Within just a few hours, all the firm's data is restored from a recent, secure cloud backup. Attorneys simply log in from home and get back to work, accessing every file and program they need. For their clients, it’s as if nothing ever happened.
A real business continuity plan is your firm’s playbook for a crisis. It must include:
- Regular, Automated Backups: You need copies of your data both on-site for speed and in the cloud for safety.
- A Clear Communication Plan: How will you tell your staff and clients what’s going on?
- Defined Recovery Objectives: How fast do you need to be back online (Recovery Time Objective) and how much data from the last few hours can you afford to lose (Recovery Point Objective)?
- Annual Testing: A plan you haven't tested is just a piece of paper. You have to run drills to find the weak spots before a real disaster does.
Ultimately, a tested continuity plan is what allows your firm to weather any storm, protecting your revenue, your reputation, and your duty to your clients.
Leveraging AI and Automation in Your Practice
Artificial intelligence and automation aren't futuristic concepts from a sci-fi movie anymore; they're practical, powerful tools that are already changing how legal work gets done. The conversation has thankfully shifted from "Will AI replace lawyers?" to "How can AI augment lawyers?" The answer is simple: by acting as a powerful assistant that handles the repetitive, time-consuming tasks, freeing you up to focus on high-value strategic work.
This is a huge part of what modern IT solutions for law firms are all about.
Instead of getting lost in the hype, let’s talk about what these tools can actually do for your firm right now. Imagine feeding an AI platform thousands of documents for e-discovery and having it flag the most relevant information in minutes—a job that would take a team of paralegals weeks to complete. Or, think about automation tools that handle client intake, schedule appointments, and send out reminders, freeing up your administrative staff for more important duties.
A Cautious but Necessary Step Forward
Despite all this potential, many firms are hesitant to dive in headfirst, and for good reason. The ethical considerations, data privacy concerns, and the very real risk of inaccurate AI outputs are serious issues. You absolutely need clear, firm-wide policies before you even think about implementation.
The key is to approach AI strategically. It’s not a magic bullet; it's a specialized tool that requires human oversight.
Recent data shows this cautious approach in action. The 2025 AffiniPay Legal Industry Report found that only 21% of law firms reported using generative AI tools. That's actually a slight dip from 24% the previous year. This is a sharp contrast to individual adoption, where 31% of legal professionals now use these tools in their daily work. This suggests a major gap between personal use and official firm policy. You can read more about these AI adoption trends in the legal industry.
The goal isn't to be the first to adopt every new AI gadget. It's to be the smartest—implementing technology that is secure, ethically sound, and provides a clear return on your investment.
A Practical Blueprint for AI Implementation
So, where does a firm even start? The most successful approach we've seen is to begin with small, focused pilot programs. Don't try to overhaul your entire practice overnight. Instead, identify a few specific, high-impact tasks where AI can make a measurable difference.
Here are a few ideal starting points:
- Legal Research: Use AI-powered platforms to quickly summarize case law, find relevant precedents, and analyze statutes. This can dramatically speed up your research process.
- Document Review: Deploy tools to scan contracts or discovery documents for specific clauses, inconsistencies, or key terms.
- Drafting Initial Documents: Use AI to generate first drafts of standard documents like NDAs or simple contracts, which an attorney can then quickly review and refine.
This methodical approach lets your firm manage risk effectively. By starting small, you can test out different tools, develop best practices, and ensure ethical compliance in a controlled environment. Most importantly, it allows you to demonstrate a clear return on investment (ROI) to partners and stakeholders, building the confidence you need for a wider rollout.
When managed properly, AI and automation become powerful tools for gaining a real competitive advantage.
How to Partner with the Right IT Provider
Picking an IT partner is one of the biggest decisions your law firm will ever make. This isn't just about fixing printers; it's a choice that directly impacts your security, your team's efficiency, and your fundamental ability to maintain client trust. It’s time to stop thinking of IT as a cost and start seeing it as a strategic investment in your firm's future. The right partner is the foundation for everything.
A true technology partner for a legal practice does more than just fix broken computers. They get the ethical and operational pressures you face every day. They should act as a strategic advisor, helping you cut through the noise and navigate the complexities of modern legal tech.
Your Vetting Checklist
To find the right fit, you have to ask the right questions. Think of the core IT pillars we've discussed as a framework for vetting potential providers. This is how you ensure you find a team that can deliver the comprehensive support your practice actually needs.
Here’s what you need to look for:
- A Secure Infrastructure Plan: Can they build and maintain a network that's both fast and resilient? The goal is minimal downtime and maximum productivity for your attorneys and staff.
- Robust Cybersecurity Expertise: Do they offer a multi-layered security plan? This should include proactive monitoring, employee security training, and advanced tools to detect threats before they cause damage.
- Efficient Cloud and Document Systems: Can they guide you to the right legal-specific cloud platforms and document management systems? These tools must meet compliance standards and genuinely make your workflows smoother.
- A Tested Recovery Plan: Do they have a clear, well-rehearsed business continuity and disaster recovery plan? You need to know exactly how they'll get your firm back online after any kind of disruption.
Choosing an IT provider is about finding a long-term partner who understands your firm's unique obligations. Their expertise becomes your firm's competitive advantage, safeguarding your reputation and enabling you to focus on practicing law.
Finding a Partner, Not Just a Vendor
A vendor sells you a product; a partner invests in your success. They should be able to speak your language, understanding concepts like "ethical walls" and "chain of custody" without needing a dictionary. They need to be proactive, spotting potential issues long before they escalate into firm-wide emergencies.
Ultimately, the best IT solutions for law firms come from a provider who offers something more valuable than just technical skill. They offer peace of mind. For firms looking for this level of dedicated support, exploring professional managed IT services is an essential step toward building a more secure and successful practice.
Keep your business running without IT headaches.
GT Computing provides fast, reliable support for both residential and business clients. Whether you need network setup, data recovery, or managed IT services, we help you stay secure and productive.
Contact us today for a free consultation.
Call 203-804-3053 or email Dave@gtcomputing.com
Article created using Outrank


